While many dark web websites, like the former black market website Silk Road, are used to facilitate criminal activity, there are also plenty of legitimate dark web websites. ProPublica is a non-profit, Pulitzer Prize-winning news outlet that focuses on abuses of power and issues of public trust. ProPublica’s investigative journalism can upset powerful interests, so the outlet joined the dark web to help their journalists and readers access their content anonymously. Being on the dark web also lets whistleblowers send material to ProPublica without fear of reprisal.
Experimental Technologies And Decentralized Networks
It is designed to ensure user anonymity while offering access to a diverse array of information available on the dark web. This is especially beneficial for professionals in cybersecurity or research, who require quick access to specific types of information. As stated above, we don’t condone any activity—on the dark net or otherwise—that is forbidden by law. Activists, whistle blowers, and journalists also use the dark web to communicate securely with sources and news organizations. Wasabi Wallet is a Bitcoin wallet that not only hides all your data in the Tor network but also allows you to “join” your transactions with others to increase your anonymity.
FAQs About Navigating The Dark Web Safely
No longer restricted to dial-up, many of us now consider access to a stable high-speed internet connection a critical element of our daily lives. We pay our bills online, check our bank statements, communicate via email, find information, and maintain a presence on social media. The dark web offers powerful privacy tools, but it also hosts real dangers—from malware and phishing to deanonymization and law-enforcement traps.
Understand Legal Risks
Its server network is widely extensive, and it has state-of-the-art encryption, prevents IPv6 and DNS leaks, and ensures privacy with a no-logs policy. You can have your money back if ExpressVPN fails to impress you, leveraging its 30-day money-back guarantee. While this VPN may look slightly overpriced, considering a monthly fee of $8.32, it offers enough features to justify this rate. In short, using a VPN makes it difficult for anyone to determine who you are or where you’re browsing from.
I2P (Invisible Internet Project)
The listed links were well-grouped for a simpler browsing experience. Dark web links can change frequently, so always verify addresses from multiple trusted sources before visiting any .onion site. The links shared in this guide were working during testing, but legitimate services occasionally move to new URLs to enhance security. I recommend bookmarking verified links rather than relying on search results. Avoid entering any real personal details or using existing accounts on dark web sites.
The Best Tor And Onion Links
Despite all the dangers, there are actually advantages to using the dark web. It’s a way to access a more open internet since the dark web is decentralized. You’d also enjoy anonymity and privacy thanks to Tor’s encryption and routing, something you don’t get from most normal browsers. But, of course, exercise caution and stay away from anything illegal.
Surfshark supports unlimited simultaneous connections to protect as many devices as possible. Also, try its services risk-free with the 30-day money-back guarantee. A budget-friendly VPN service allowing users to access dark web safely anytime, anywhere, and on any number of devices they want. The Tor browser allows you to browse the internet anonymously and visit inaccessible sites. Unfortunately, others are fake and fraudulent websites that exploit the reputation of the dark web to con people.

Use Encrypted Cloud Storage And Docs
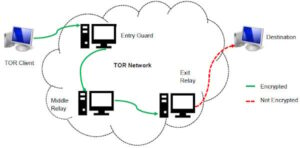
Accessing the dark web isn’t like surfing the web everywhere else online. Since you cannot access a library of dark web links using the regular Internet, you can check out platforms dedicated to indexing these sites, like The Hidden Wiki. This browser is the most suitable option for accessing the dark web, thanks to its multiple layers of encryption. Each time you connect to a dark web link, your request and traffic are routed through at least three different server points, ensuring your IP remains hidden.
Developer Tools
- LifeLock notifies you if we find your personal information on the dark web, and we’ll help you run damage control with assistance from legal experts and recovery specialists.
- However, extra caution is advised—use a good VPN and ensure the security settings of your device are up to date to minimize risks.
- Dark Lair allows you to post comments, share music, upload photos, message your dark web ‘friends’, and everything in between.
- Before diving into the dark web, ensure your security with a VPN like Forest VPN.
- These range from infections, unauthorized access, espionage, and phishing, to the theft of sensitive information like customer and financial data, intellectual property, and more.
This process masks your IP address and encrypts your data, allowing you to visit websites that are not accessible via standard browsers, including .onion sites like the Hidden Wiki. To get started, visit the official Tor Project website and download the browser for your operating system—Windows, macOS, Linux, or Android. Avoid downloading the browser from unofficial sources to prevent malware or tampered versions. Once installed, the browser is simple to launch, and it automatically connects to the Tor network. This connection can take a few moments, depending on your internet speed and network conditions.
There is no way to opt out of having your personal data used this way. Google claims it anonymizes data before using it and doesn’t show you personalized ads based on the content you have in Google Drive, Docs, Sheets, Slides, or Photos. At Proton, giving you the ability to easily protect your privacy and most sensitive, valuable information in your digital life is central to everything we do.
As we’ve seen, technologies like Tor, I2P and privacy coins empower users to bypass censorship, protect sensitive communications and maintain control over personal data. At the same time, the same infrastructure facilitates illicit trade, malware distribution and identity theft. The line between privacy and peril is often one of intent—and operational discipline. SecureDrop and similar onion services give insiders a safe conduit to expose corruption or safety lapses without risking employer surveillance. Because traffic never leaves the Tor network, neither Internet service providers nor platform operators can easily trace the sender—crucial protection in sectors where retaliation is swift.
Is It Legal To Access The Deep Web?
- If you’re trying to hide from an oppressive government or want to be a whistle-blower for something illegal, take as many steps as you can to be safe.
- The US Supreme Court has indicated that even casual browsing could lead to legal consequences.
- The dark web draws not only serious cyber criminals but also law enforcement agents aiming to catch them.
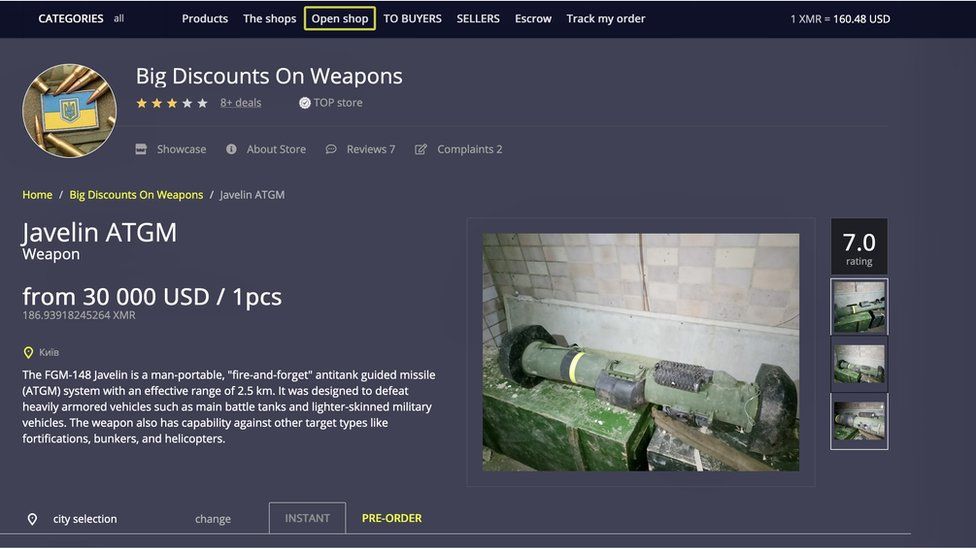
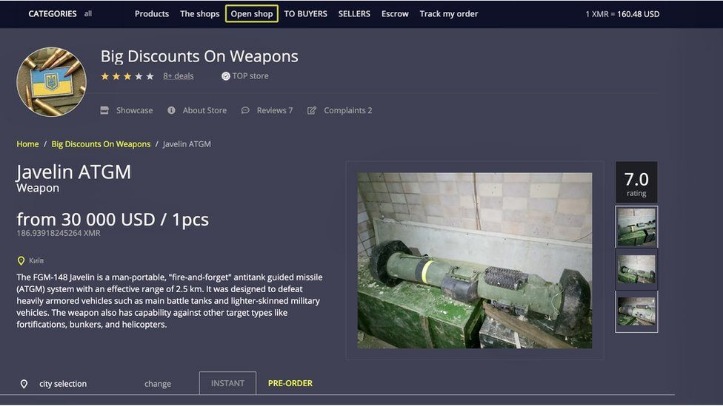
- All of this has made it one of the most reliable markets still active in 2025.
- However, this also means that navigating the dark web can be slower due to the extensive encryption involved.
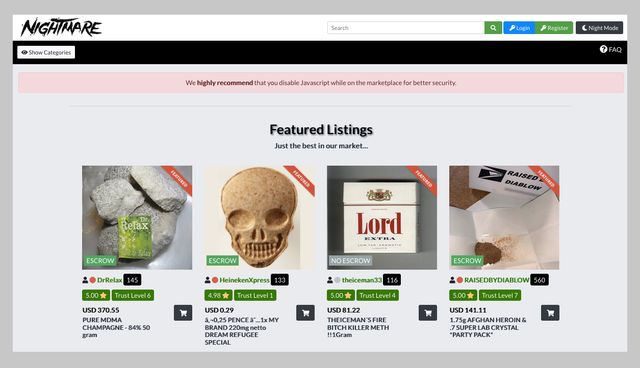
The surface web (often referred to as the “visible web”) is the portion of the web available to the general public and indexed in the standard web search engines such as Google, Bing, and Yahoo. When venturing into the dark web, it is crucial to prioritize safety by educating oneself about potential risks and employing robust security measures to protect data and maintain privacy. With tools like Cyble Vision, it helps organizations stay protected of cyber threats, including dark web monitoring, providing critical insights for better cybersecurity management. The Excavator search engine digs through the depths of the dark web, offering an expansive view of indexed content. One of the oldest and most robust dark web search engines, the Torch search engine is known for being fast, straightforward, and acting as an unblocked search engine with minimal filtering. Pastebins are text sharing services, useful for sending and sharing large snippets of code or text.
Different dark web search engines cater to various needs, offering varying levels of privacy, security, and ease of use. It’s specifically designed for privacy, routing your connection through the Tor network to hide your IP address and encrypt your traffic. Built-in features like script blocking and anti-tracking ensure a safer browsing experience. The dark web is home to the internet’s hidden sites, services, and products — some innocent, others downright dangerous.
Also, you can set a strong password to protect your message and choose how long it will take to expire. This service is a good source of statistics if you have a school project requiring research on Tor and the dark web. However, note that the site only uses non-sensitive and public data for the metrics. The Tor Metrics is a good place to get more information about the Tor project. It collects data from the public Tor network and archives historical data of the Tor ecosystem. This means you can visit the site anonymously using the Onion browser, especially if you live under an oppressive regime.