Meanwhile, cybersecurity experts monitor the dark web, scanning for stolen data and emerging threats. If your information surfaces in these murky depths, there’s very little you can do – but knowing the risks involved is a first step toward defence. From information security threats like identity theft and malware to scams and surveillance, navigating the dark web without caution can lead to real dangers. So, is the dark web a lawless underworld or a misunderstood frontier for privacy and free expression? Tor was initially developed by the US Navy to facilitate secure communication for informants. Similarly, the CIA launched its .onion site to provide worldwide anonymous access to its resources.
What Is The Best Search Engine On The Dark Web?
Avast SecureLine VPN encrypts all of your internet traffic to help block hackers and keep snoops out. Install Avast SecureLine VPN today to browse safely and securely, wherever your online travels take you. A lot of illegal activity occurs on the dark web, and onion websites are popular hangouts for cybercriminals and scammers. But if you use antivirus software, avoid clicking shady links, and stick to known sites you should be okay. It’s also a good idea to set up a VPN for an extra layer of protection.

FAQs On The Best Dark Web Search Engines

Unlike traditional search engines, it doesn’t track or store personal information, ensuring your searches stay private. It’s a popular choice for users worried about online surveillance and data collection. Dark web websites are pages that exist on a part of the internet that isn’t indexed by traditional search engines like Google. Also known as deep web sites, these pages typically have URLs ending in .onion and are only accessible through special software like the Tor Browser.
Hackers spend a lot of time on the dark web, and it’s not too difficult to get access to hacking tools and data leaks in this part of the internet. However, it’s much harder to get at the people who are doing the uploading and downloading. Open up Tor, and you won’t suddenly see the dark web staring back at you.
Social media platforms like Facebook and news sites like the BBC and ProPublica have also waded into the dark web’s waters. These legitimate media companies keep a presence on the dark web to help users who might, for a variety of reasons, have difficulty accessing their content on the open web. In the internet’s darkest corners, a myriad of hidden websites cater to an array of needs and interests.
How Do I Open Onion Links?

By understanding its structure and ensuring safe browsing practices with tools like Forest VPN, we can navigate this digital underbelly responsibly. Whether you’re exploring for curiosity or necessity, the dark web reminds us of the dual nature of technology—empowering yet enigmatic. Dark Storm Team is a politically motivated group that uses Telegram to broadcast its cyber activities. It frequently shares updates about claimed attacks on public and private sector targets, including infrastructure, transportation, and government systems. The group also promotes DDoS services and seeks visibility for its operations through proof-of-attack screenshots.
The Abacus Market links to the new dark web marketplace sections and took over much of the vacuum left by the AlphaBay takedown. Security researchers have been monitoring forums within the cybercriminal underworld to investigate the leading markets operating in 2024. Never log in with your real name or reuse passwords from other accounts.

Update Your Tor Browser
Users of the dark web should also realize that although their activity is technically anonymous, associating with people who are conducting illegal activities can have legal implications. With access to such crucial data, cybersecurity professionals can detect threats earlier, identify data leaks, and take proactive hardening measures to prevent or stop active breaches. Leveraging real-time visibility into Telegram will empower cyber pros to rapidly respond thus reducing the risk of critical security incidents. One study found that only 6.7% of Tor anonymity network daily users — a cohort that comprises mostly dark web users — connect to onion sites used for illicit activity.
How Can I Stay Safe While Browsing The Dark Web?
For those needing an additional layer of security, you can set it to disappear right after viewing. Onion.name is a dark web resource that helps make sense of the mess of letters and symbols that usually form the darknet sites. Just like Facebook, this is no random namesake; it is a legitimate platform from which to reach the CIA anonymously. You can even apply for jobs and request information, among other things.

Is There A Tor Browser For Android?
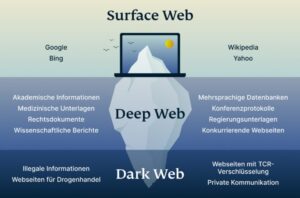
- Examples of the deep web include any websites that are behind a paywall or require login credentials.
- It hosts encrypted websites, often used for privacy, anonymity, or illicit activities.
- We are reader supported and sometimes earn a commission if you buy through a link on our site.
- In addition, know that while accessing the dark web is legal in most countries, engaging in illegal activities (buying or selling contraband, hacking services, etc.), is illegal everywhere.
- Tim Berners-Lee, one of the founders of the World Wide Web, is currently involved in its operations.
Most internet users want to use the dark web safely, but it’s still important to be careful when using any onion browser. Privacy-focused internet users who access onion sites may see greater anonymity while browsing or sharing sensitive information. These pages can also help circumvent some forms of government censorship. Keybase is a secure platform that lets people chat, share files, and collaborate — kind of like a privacy-first version of cloud storage service Dropbox or communication platform Slack.
They use pseudonymous wallets, privacy coins (like Monero), mixers, chain-hopping, and non-KYC platforms to obscure transaction trails. Cybersecurity experts should pay close attention to these trends, as they often indicate emerging threats and profit-generating tactics among the cybercriminal forums. Active for a decade since 2014, it is a widely used credit card shop used to source stolen credit card information such as dumps, CVVs, Wholesale Accounts. The US government created the dark web to help its spies communicate and exchange information securely.
However, due to copyright infringement, Sci-Hub is considered illegal and banned in many countries. Founded around 1999 by activists in Seattle, it has since grown to over six million users worldwide. It publishes a newsletter in multiple languages and not only runs onion services for its website but all its email and chat services. Unlike Ahmia and Haystak, however, DuckDuckGo doesn’t search .onion sites.
DuckDuckGo’s regular site can take you to the dark web, as it brings up onion sites and dark web links when searched. Neither DuckDuckGo’s dark nor normal versions keep a log of your web activity. The dark web is a hidden part of the internet where users are anonymous and can access illegal marketplaces and hacking forums and partake in illicit activities. In some cases, it’s also used for private messaging, cybersecurity training, whistleblowing, and other legitimate uses. Accessing the dark web is not inherently illegal in many jurisdictions.
Based on our observations from analysis on dark web data using Lunar, we’ve identified the top 7 marketplaces on the dark web in 2025. We developed Lunar to monitor the deep and dark web, including dark web marketplace sites. Opening the onion links is very easy from the Tor browser, which you need to download and install in advance. To search for onion links for any website on the surface web, just copy-paste the URL in a Tor browser window.
Tor anonymity comes with a cost since malicious hackers and criminals like to operate in the shadows. For example, perpetrators of trafficking and cyber attacks use the dark web to disguise their actions. Furthermore, it’s critical to understand that Whonix is not a stand-alone browser. It is a component of Whonix, an operating system that functions as a whole inside a virtual computer. It includes all the essential productivity software, including MS Word and an email client.