Five Greek teenagers were brought before the main court of Rhodes last week to answer for allegedly supplying, possessing, and distributing counterfeit money. The investigation into the counterfeit money circulating on Rhodes began in September 2018 but has taken until now to come to a head. In September 2018, Austrian authorities worked with Polish police to dismantle another money counterfeiting network operating in the Polish city of Gdynia. Austrian police have played a major role in the past two years when it comes to bringing down counterfeit money printing shops operating on the Dark Web. According to Europol, the suspect’s shop was capable of printing 10, 20 and 50 euro banknotes.
US Takes Down Illegal Cryptocurrency Mixing Service Samourai Wallet
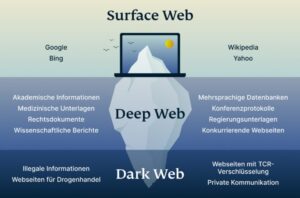
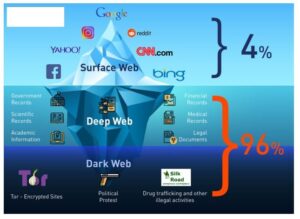
Thus, estimation of product origins from dark markets and measures of seized goods might also vary because they capture products at different supply chain stages. Cryptocurrencies like Bitcoin, Ethereum, and Monero are commonly used on the dark web. Their decentralized nature and cryptographic security make them attractive for anonymous transactions (Alessa). The dark web markets offer a wide range of illicit goods and services, including stolen data, drugs, weapons, hacking tools, malware, counterfeit currency, and personal information, all traded for virtual assets like Bitcoin.
Knowing which counterfeits are offered on darknet markets could help companies to make those products more difficult to counterfeit. For example, companies could change the used materials or manufacturing process to increase the efforts of imitating the product. Traceability of genuine products within a supply chain would also fall within that category, as it increases the efforts needed to counterfeit them, which could be technologically facilitated (Gayialis et al., 2022).
How Is Counterfeit Money Sold On The Dark Web?
During the 300 house searches, authorities also found drugs, weapons, Bitcoins, hardware for mining virtual currencies, a cannabis plantation, but also an additional illegal euro counterfeit print shop –the last two located in France. Most of the remaining categories contribute only a little, with most representing only 2% or less of all counterfeits. Thus, almost 80% of counterfeits listed were represented by only five (of the 16) categories of products. Inspired by previous research (Wegberg et al., 2018), we used the annotated listings to train a multiclass classifier to predict the labels of the remaining unlabeled counterfeits.

Why Buy Counterfeit Money From Dark Web Notes?

In addition, we sampled ten darknet market products from each category and determined their price on the surface web (Table 9). Since we selected only ten random samples for each product category, the estimated price differences are only intended to illustrate the observed trend and should not be regarded as a complete analysis. Despite the perceived anonymity of cryptocurrencies like Bitcoin, law enforcement leverages advanced blockchain analysis tools (such as Chainalysis and Elliptic) to track transactions from dark-web markets back to real-world identities.
Holding And Placeholder Prices
Many maximum prices of each counterfeit category are high, often attributed to wholesales. The highest observed mean price is for metals, including collectible gold and silver coins or bullions, while the lowest is for sunglasses. With watches making up most listings, they also hold the highest volume, around 1 million USD.
Common Scams On Dark Web Marketplaces
These marketplaces are often accessed using special software, such as the Tor browser, which allows users to browse the dark web anonymously. Once a buyer has found a seller who is offering counterfeit money, they can typically make a purchase using cryptocurrency, such as Bitcoin. Illicit marketplaces on anonymous networks allow fraudsters to set up fake business-to-business (B2B) platforms. Unsuspecting companies seeking scarce goods may engage with these fraudulent vendors, leading to payments for non-existent products or services.
Dark Web Vendor Of Opioids And Counterfeit US Currency Pleads Guilty

The python package “nltk” (Bird et al., 2009) was used for all text cleaning and feature generation steps. To increase the classifier’s performance, we used a mix of under- and over-sampling methods to balance the number of product listings between the categories. First, the category “Watches” was under-sampled, reducing the number of listings in the sample. This was followed by oversampling of the remaining categories to increase the number of these listings in the sample, resulting in an equal representation between all categories, each consisting of 450 listings. To reduce the number of listings within each category, we randomly selected listings (without replacement) from the data until we reached 450 listings. To increase the number of listings within a category, we used “SMOTE” (Synthetic Minority Oversampling Technique), which synthesizes new unseen data points (Chawla et al., 2002).
How VPNs Are Helping People Evade Increased Censorship – And Much More
- In 2023, the dark web attracted an average of 2.7 million daily users, with Germany now leading as the country with the highest number of Tor users, surpassing the United States for the first time in years.
- Without a proactive cybersecurity strategy, businesses risk severe financial losses, reputational damage, and even legal repercussions due to compliance violations.
- “As far as marking them with the pen, they would mark true as a good one hundred dollar bill but the texture of the bill was different.”
- We then (V) compare our results to observations made through border seizures, complaint statistics, and activities from authorities to contribute to the overall understanding of the counterfeit economy.
Investigators say the counterfeit money is starting to show up all over the southeast and they can’t say yet how many more cases are going to come out of the investigation. Aldon, they revealed, has a criminal history and other scams under investigation by federal agencies, including counterfeit money passed in North Carolina and money order fraud in South Carolina. Your personal information — like passwords, Social Security Numbers, or credit card details — can end up on the darkweb if a company you use suffers a data breach. Using tools like the Tor browser to browse hidden sites is allowed — it’s just a way to stay anonymous online. Once you step inside the dark web, you’ll find a hidden network where stolen data changes hands every day. Cybercriminals use it to trade Social Security Numbers (SSNs), passwords, hacked email accounts and even entire identity kits.

However, cybersixgill’s statistics reveal a market largely dominated by a small number of big players with the top 10% of sellers accounting for 80% of counterfeit note listings. Please note that personal data collected through this form is used and stored for the purposes of processing this report and communication with you. Much research and intervention focuses on electronic money laundering and large scale counterfeiting.

Some markets are invite-only or have strict registration rules to keep out scammers and law enforcement. There’s also a privacy angle—some users live in countries with censorship or surveillance, and the dark web gives them a space to communicate or access information more freely. It’s been a constant back-and-forth between cybercriminals and law enforcement, with each new site trying to be smarter and more secure than the last. For instance, cybercriminals can buy credit card details with a $5,000 balance for just $110. As of 2020, nearly 57% of the dark web was estimated to contain illegal content, including violence and extremist platforms.
Furthermore, criminals may employ shell companies and offshore accounts to move money across borders and disguise its origins. These methods make it difficult for authorities to detect and prevent money laundering activities on the dark web, posing a significant challenge for law enforcement and financial institutions. One of the primary reasons Dark Web marketplaces thrive is the anonymity provided by Tor and cryptocurrency transactions. Tor encrypts internet traffic through multiple layers, making it difficult to trace users, while cryptocurrencies like Bitcoin and Monero enable pseudonymous financial exchanges, reducing the risk of detection by authorities.
He is accused of distributing 25 notes to the other 16-year-old who was involved in navigating the dark web. The other notes were allegedly sold to a third 16-year-old as well as a 15 and 17-year-old. When investigators searched the homes of the individuals involved, counterfeit notes were found in the two 16-year-olds’ homes.