A piece of tape over your webcam essentially prevents any possible remote activation by malware. Assume that everyone and every site is trying to take advantage of you. Avoid giving up real information, don’t log into your personal accounts, and don’t engage in conversations that could identify you.

Download Norton 360 Standard For Windows—Complete Cybersecurity For Your PC
When you install a VPN, all of your activities on the dark web will be hidden from unwanted snoops from your ISP or the FBI. The VPN is a second layer of extra protection, on top of the protection that the Tor network already offers. The core principle of the Tor network was first developed by U.S. Naval Research Laboratory mathematicians and computer scientists in the mid-1990s.

By The Tor Project
The dark web has no shortage of criminal activity, scams, phishing sites, suspicious links, and malware designed to trick newbies. Links posted to the clear web, in particular, are often malicious. And because there’s very little use of HTTPS on the dark net, verifying whether or not a website is genuine using an SSL certificate is not feasible. If you want to use Tor privately, you can use either a VPN or Tor Bridges (Tor nodes that are not publicly indexed).
The Dark Web can’t be easily stopped or shut down due to its decentralized nature and the use of technologies like Tor. The dark web contains much of the internet’s illicit content, ranging from drug trafficking to child pornography sites. Setting up I2P requires more configuration on the user’s part than Tor. I2P must be downloaded and installed, after which configuration is done through the router console. Then individual applications must each be separately configured to work with I2P. You’ll need to configure your browser’s proxy settings to use the correct port on a web browser.
How To Access The Dark Web: Step-by-Step Tutorial (and A Few Words Of Caution)
However, there are plenty of legal and legitimate online activities that require privacy and anonymity. The dark web is used by journalists, whistleblowers, and political activists who need the protections that it offers. Anything you need to do that has to be off the books to some extent, for noble or ignoble reasons, can be done on the dark web. Although content on the dark web is not as ‘indexed’ compared to the one on the clear web, you can still use search engines to find stuff. At first glance, Tor doesn’t look that different from your regular browser – it has a search bar, lots of quick-launch icons, the peeled onion icon smack in the middle of the screen.
Digital Hygiene And Best Practices
The browser is available for Linux, macOS, and Windows desktop and laptop computers. A Tor Browser from the Tor Project is available for Android, and The Onion Browser from developer and journalist Mike Tigas is available for iOS mobile devices, which the Tor Project links to. If you are reading this, you’ve likely heard about how the Tor Browser can help protect your internet privacy and anonymity online. Simply accessing the dark web and using the Tor browser may already raise government suspicion.
Monitor Your Traffic Routing
With Dark Web’s built-in dark mode support, you can use any search engine or access a social media platform without straining your eyes. Its voice search functionality, though is a nice touch, making content searching more convenient. However, users should remember that the app doesn’t come with a bookmark function. Other standout features of this app include voice search functionality and a convenient QR code and barcode scanner. Plus, you can stay private while browsing as it doesn’t store your internet history. However, you can’t bookmark websites or access the “Settings” page.
Will Visiting The Dark Web Attract Attention?
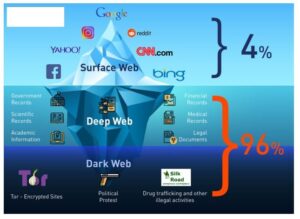
Darknet allows you to access the dark web and its hidden resources securely. It enables navigation through Onion websites and ensures an anonymous browsing experience by shielding online activity from third-party surveillance. Whether you are exploring academic content, legal data, or unique marketplaces within the dark web, the app’s structure ensures user safety and discretion. While it’s generally safe to use, dark web activity can be detected at the entry and exit nodes of the Tor network. The Dark Web, Darknet, and Deep Web are distinct parts of the internet, each defined by its accessibility and the level of anonymity. The Deep Web is the vast part of the internet not indexed by search engines, encompassing everything that doesn’t appear in search results.
Unfortunately, some oppressive regimes have figured out a way to block Tor traffic. Using a VPN in conjunction with the Tor Browser is an excellent way to keep your online travels secure and private. A VPN’s ability to hide your Tor usage from your ISP and from government authorities makes for a valuable addition to your online privacy arsenal. Also, since the Tor Browser is based on the Mozilla Firefox platform, it’s susceptible to the same attacks that other browsers are. While the Tor Browser and the Onion Network are an excellent way to protect your online privacy and anonymity, it is by no means a perfect solution, and it has a few weaknesses.
Review Of The Best Browsers For Dark Web Access In 2025
Tor Browser has since become a popular tool of journalists, activists, and others that may be subject to being monitored online. If top-notch privacy is your goal, yes, you can use the Tor Browser for all of your browsing. Just remember, this only hides your browser-based activities and doesn’t hide any of your other online activities.
- Having robust antivirus protection adds an essential layer of security, helping to ensure your device and personal information remain safe while navigating the Dark Web.
- On its own, Tor obscures your IP address by bouncing online requests through multiple servers, similar to how a VPN routes your traffic through an external server.
- To connect manually for the first time, click on the Connect button on the homepage and wait for Tor to establish a connection.
- Digital surveillance and cybercrime continue to rise, underscoring the need for disciplined cybersecurity habits.
- This article highlights the easiest ways to configure the Tor browser on any OS.
- Tor was developed in the mid-1990s by United States Naval Research Laboratory employees, mathematician Paul Syverson, and computer scientists Michael G. Reed and David Goldschlag.
As you are now familiar with the three different sections within the entire world wide web, let’s take a closer look at how you can access the dark web anonymously. Those who access the dark web do so via the Tor (The Onion Router) browser. Absolutely no one knows who’s surfing on the dark web, who is selling, who is buying or anything like that – as long as you take the correct safety and online privacy precautions. The dark web is infamous for containing sites such as Silk Road and other marketplaces where users could potentially buy drugs and/or weapons, stolen credit cards, IDs, and much more. The majority of the web is called the “deep web” (often referred to as the “invisible” or “hidden” web). The deep web is basically all the content that you can’t find using Google or Yahoo search.
- It is therefore highly recommended to use VPN software to get onto the dark web safely.
- Our rigorous research and testing have revealed revealing truths and busted myths.
- This can prevent your data from being intercepted in this segment of the connection, which might be a concern in certain scenarios, such as using unsecured WiFi networks.
- The Invisible Internet Project (often shortened to I2P) uses garlic routing, a variant of Tor’s onion routing protocol.
- Alternatively, users can connect in opennet mode, which automatically assigns peers on the network.
- While it’s generally safe to use, dark web activity can be detected at the entry and exit nodes of the Tor network.
While it’s not a browser, it includes Tor Browser installed by default that provides anonymity for web browsing and enables users to access the dark web. Combined with the browser, it will provide maximum security and anonymity online. A VPN routes your online traffic through secure and encrypted servers to ensure you stay anonymous, unseen, and untraceable. It does this through high-level and top-quality encryption, providing you with an extra layer of protection at all times. To find what you’re looking for, you may need to try multiple search engines or visit directories of trusted .onion links. If you need an idea of where to start, check out our list of the best dark web sites in 2025.
Because it’s easier to contain malware in a virtual environment, which can be fully controlled. Well, VPN over Tor is basically its opposite – instead of going through the VPN first, the signal passes through the Tor network, before going through the VPN. Tor relays are servers run by volunteers, designed to keep your activities private and untraceable.