
Fullz includes full personal details as well as financial details such as bank account details or social security numbers, which can be used for a full account takeover or identity theft. Since the WhatsApp privacy policy controversy in January 2021, Telegram rapidly gained traction as a privacy-focused alternative, attracting users seeking secure communication channels. However, its growing popularity also caught the attention of threat actors, who recognized its potential as a dark web-adjacent platform for facilitating cybercrime operations.
In 2025, finding the best CVV shops feels like navigating a minefield of scams, Telegram caps, and dead dumps. The old days of reliable, valid CC hits, easy non-VBV BINs, and weekly vendor drops have evolved. Not all the above details are available for all 1.2 million records, but most entries seen by BleepingComputer contain over 70% of the data types.
Get Threat Assessment Report
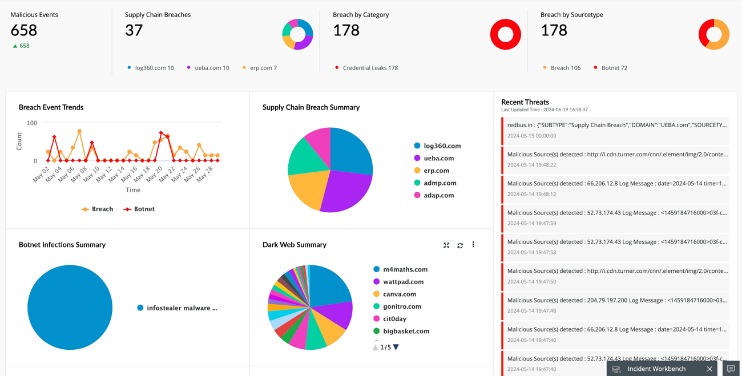
Card data is a hot commodity on the dark web, with credit card details and cloned cards being sold to cybercriminals. These stolen cards can be used for financial gain through unauthorized charges, account takeover, and identity theft. As cybercriminals continue to exploit dark web markets, Telegram channels, and underground forums, organizations must take a proactive approach to identifying potential risks.
Censorship-Resistant Content On The Hidden Wiki
However, users should still exercise caution as no directory is entirely immune to malicious links. Dark.fail’s clean interface and commitment to regular updates make it an excellent choice for users seeking safer navigation of the dark web. It has built a reputation for being a reliable source of stolen credit card data and PII. Renowned for its extensive inventory of financial data and sophisticated operating methods, Brian’s Club is a key player in the underground economy of financial cybercrime. Launched in 2023, STYX focuses on financial crime, providing stolen credit card data, hacked bank accounts and access to various cryptocurrency laundering tools.
- The BidenCash marketplace specialized in carding—the trade of stolen credit card data—and also sold compromised credentials, including Secure Shell Protocol (SSH) access for unauthorized server entry.
- You are responsible for reading, understanding, and agreeing to the National Law Review’s (NLR’s) and the National Law Forum LLC’s Terms of Use and Privacy Policy before using the National Law Review website.
- Its commitment to privacy, diverse product offerings, and robust security measures make it a preferred choice for users seeking discreet transactions within the darknet.
- It is a hub for financial cybercrime and offers a wide range of illicit services and stolen data that cater to sophisticated cybercriminals.
- Here we discuss cryptoasset compliance, blockchain analysis, financial crime, sanctions regulation, and how Elliptic supports our crypto business and financial services customers with solutions.
Hosting & Development: Daniel’s Hosting, OnionShare, Tor Project Onion
Because of the level of anonymity, these sites allow cybercriminals, it is critical to use powerful dark web monitoring tools, such as Webz.io’ Lunar, to track emerging financial and reputational threats. While Telegram was once a safe haven for illicit activity, recent policy changes have forced many threat actors to reconsider their presence on the platform. In September 2024, Telegram introduced AI-based content moderation, making it more difficult for cybercriminals to share and access illegal materials. Many hacktivist and cybercriminal groups have since started migrating to alternative platforms, such as Signal, Discord, and decentralized messaging networks. The Hidden Wiki is primarily used as a directory of dark web .onion links, helping users navigate various hidden services such as marketplaces, forums, email providers, and whistleblower platforms.
Using A VPN For Additional Security
The phrase “dark web” conjures images of illegal activity, but it simply refers to the encrypted part of the Internet that isn’t indexed by search engines. Experts suggest that this giveaway serves as a marketing ploy to attract new users to B1ack’s Stash and establish its dominance in the competitive carding market. Breachsense monitors the dark web, Telegram channels, hacker forums, and paste sites for external threats to your organization. Financial institutions tighten their security measures to prevent fraud but that also prevents legitimate transactions as a result.
- A dump of hundreds of thousands of active accounts is aimed at promoting AllWorld.Cards, a recently launched cybercriminal site for selling payment credentials online.
- Dark.fail has become one of the most trusted alternatives to the traditional Hidden Wiki.
- Just in the last 3 months millions of unique credit card credentials have circulated across the deep and dark web.
- Cyberthreats are constantly evolving, and your security measures should be continuously updated as well.
- The dark web, shrouded in anonymity and lacking regulation, serves as a breeding ground for criminal activity.
- The cards were published on an underground card-selling market, AllWorld.Cards, and stolen between 2018 and 2019, according to info posted on the forum.
In addition, the Hidden Wiki provides links to essential privacy-focused services, such as encrypted email providers, anonymous messaging platforms, and cryptocurrency tools that help maintain anonymity during transactions. It also connects users to hosting services and whistleblower platforms, facilitating secure communication and file sharing on the dark web. The repercussions of dark web credit card marketplaces, including the rise and fall of Joker’s Stash, extend beyond monetary losses. Financial institutions shoulder increased operational costs tied to investigating fraudulent activities and failed authentication attempts. Customers who lose their card data to fraud may turn to a different card while waiting for a replacement card, threatening the top-card effect of passing all spending across one preferred card.
Is The Hidden Wiki Safe?
Dark Storm Team is a hacktivist threat group known for its pro-Palestinian cyber activities and past collaborations with groups such as Anonymous Sudan. The group has carried out cyberattacks against Denmark, Egypt, France, Israel, the UAE, and the United States, frequently working alongside other threat actors. The platform offers Live Traffic, delivering logs in real time, and Private Cloud, which provides up to 5,000 logs daily, amounting to 120,000 logs per month. Additionally, Omega Cloud maintains a database exceeding 2 billion records, accessible through a subscription-based model.
The stolen data reportedly includes a mix of credit and debit cards from major providers like Visa, MasterCard, American Express, and JCB. By observing how threat actors advertise and price different types of card data, we can identify which security measures they’re successfully bypassing and which ones are still effective. In this post, we’ll cover how credit card fraud operates on the dark web, how criminals obtain and trade card data, and cover some essential prevention strategies.

Freshtools was established in 2019 and offers various stolen credentials, accounts, and host protocols like RDP. It is considered a go-to site for malware purchasing, providing keyloggers, trojans, and other Malware as a Service products. STYX Market focuses specifically on financial fraud, making it a go-to destination for cybercriminals engaged in this activity. Valued at approximately $15 million, Abacus Market is one of the most lucrative platforms in the dark web ecosystem. Thank you for joining us on this exploration of credit card transactions on the Dark Web.
Card Verification Values (CVVs)
By training your employees, you can make sure they’re able to spot social engineering schemes, avoid malware, and keep their own personal information safe, as well as the information of your customers. Cyberthreats are constantly evolving, and your security measures should be continuously updated as well. This gives security teams time to adjust their defenses before new techniques become widespread. When used correctly, it provides strategic intelligence that can prevent major financial losses.
Technical Details And Data Sources
Security researchers have been monitoring forums within the cybercriminal underworld to investigate the leading markets operating in 2024. Others are looking for stolen data, hacking services, or even banned books and political content. Some are looking for illegal stuff they can’t buy elsewhere, like drugs or counterfeit documents. It was the first big site where people could anonymously buy drugs using Bitcoin, and it gained a lot of attention, until it was shut down by the FBI in 2013. Today’s cybercriminals spread their activities across multiple platforms, making them harder to track and shut down. By redirecting seized domains to law enforcement-controlled servers, authorities have disrupted a major hub for carding and credential theft, reducing the risk of further victimization.
As of 2020, nearly 57% of the dark web was estimated to contain illegal content, including violence and extremist platforms. Telegram channels supplement traditional onion sites, blurring lines between the dark web sites and more mainstream communication tools. The BidenCash takedown demonstrates the increasing sophistication and international coordination of law enforcement in combating cybercrime. The operation also included the legal seizure of cryptocurrency assets, targeting the financial lifeblood of these illicit markets. However, experts caution that many individuals whose data was sold or leaked remain vulnerable, especially if they have not updated their banking or personal information. Following the takedown, these domains now redirect to a law enforcement-controlled server displaying an official seizure notice, effectively neutralizing their use for future criminal activity.

VirusTotal Launches Endpoint That Explains Code Functionality For Malware Analysts
Additionally, we provide detailed descriptions and safety advice for each link, empowering users to make informed decisions. Unlike many alternatives that allow user submissions without thorough vetting, we prioritize quality over quantity to maintain a safer browsing experience. Our dedication to transparency and user security makes our directory a superior choice for navigating the dark web in 2025. Never share personal information, avoid clicking suspicious links, and consider using additional layers of privacy like a VPN. Hidden Wiki was originally the name of a .onion hidden service on the Tor network, hosting a directory for links to websites on the Tor dark web.



