In these cases, the law may treat temporary, browser-facilitated possession as a crime because the visit leads to the computer holding contraband material. For the open web, just type your name into Google and see what comes up. Whether this is a Linkedin profile, Facebook, social media, or any community involvement, chances are that you already have some online presence. As most malware is designed for Windows, another way to stay safe is to switch to a different operating system.

Government Monitoring

If your work or lifestyle requires you to use the dark web, however, there are ways to protect yourself. Just as you need the right tools to access the dark web, you also need the right protections to be able to stay safe on it. The dark web isn’t entirely bad, but it’s clear that it can be deeply dangerous. It’s a hotbed of crime — both physical and digital — and anyone who dares enter it would be exposing themselves to those dangers.
Dark web websites don’t bear Internet Corporation for Assigned Names and Numbers (ICANN) domains, such as .com. They use a scramble naming structure that combines a string of letters and numbers to create URLs that are impossible to remember. You can never be sure of the motive of the person operating the node that your traffic is routed through. They use pseudonymous wallets, privacy coins (like Monero), mixers, chain-hopping, and non-KYC platforms to obscure transaction trails.
What Are Some Regulatory Challenges Faced By Authorities And Agencies Relating To The Dark Web?

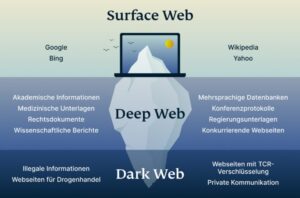
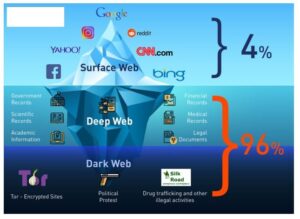
The dark web’s hazards include many risks, related to network breaches or data compromises. These range from infections, unauthorized access, espionage, and phishing, to the theft of sensitive information like customer and financial data, intellectual property, and more. Each category carries risks of devaluing enterprises through reputational damage, disrupting operations via malware attacks, or defrauding companies through theft of critical information. Designed to be hidden from conventional search engines like Google or Bing, the dark web is a portion of the internet. Access to “.onion” domains and anonymous surfing made possible by specialised software like the Tor Browser allows entry only.
Exploring The Dark Web: Understanding Its Role In Cybersecurity Threats
- Despite growing crackdowns from law enforcement agencies, the dark web remains a hotbed of criminal activity, offering everything from drugs to stolen data.
- The dark web is, at times, used as a dumping ground for personal, financial, and technical information with malicious intent.
- Tor is by far the most widely used dark web network and is the biggest network in terms of content and activities.
- It was discovered that DEER.IO not only sold details of gamer accounts but also the personal information of Americans, such as their names, addresses, telephone numbers, and even social security numbers at times.
- The CTO of a cybersecurity firm claimed that this data was sold for about 10 Bitcoin or BTC (which comes to around Rs. 4.25 crores).
Operations like “Operation Onymous,” which led to the seizure of over 400 dark web sites, demonstrate the ongoing battle against criminal content. The dark web intelligence market experiences a dynamic increase in cybercriminal operations. 4iQ reported that stolen account credentials on the dark web experienced an 82% increase in 2022 to reach 15 billion. Identity theft cases lead the dark web monitoring activities at 65% while credit card fraud follows closely behind at 15% and the number of card dumps exceeds 192 million according to Sixgill’s reports. Chainalysis researchx` Anatomy reveals dark web cryptocurrency activity almost doubled between 2020 and reached $25 billion in 2022 thus underscoring the necessity for advanced tracking systems.
The dark web often carries a negative connotation, largely due to its association with illegal activities. However, it also offers significant advantages, especially in terms of privacy and security. For individuals living under oppressive regimes or anyone needing to communicate away from the watchful eyes of surveillance, the dark web is a valuable tool. A substantial portion of users turn to the Tor browser for its promise of anonymity, while others seek the additional security it provides. Curiosity about what the dark web has to offer also drives about one-third of its users. Originally used by the United States Department of Defense to communicate anonymously, the dark web has now become a hub for users wishing to remain anonymous around the world.
What Is The Dark Web? Here’s Everything To Know Before You Access It
Darren Guccione is the CEO and co-founder of Keeper Security, the world’s most popular password manager and secure digital vault. Keeper is the first and only password management application to be preloaded with mobile operators and device manufacturers including, AT&T, Orange, America Movil and HTC. Keeper has millions of consumer customers and the business solution protects thousands of organizations worldwide. Dark web search engines exist, but even the best are challenged to keep up with the constantly shifting landscape.
Contrary to popular belief, not all activities on the dark web are illegal. Many individuals access the dark web for legitimate reasons, such as maintaining privacy and anonymity. For example, journalists and whistleblowers may use the dark web to communicate securely and protect their sources. Additionally, individuals living in countries with restrictive internet censorship may use the dark web to access information and express their opinions freely. The dark web consists of websites and content that are not indexed by search engines and require special software, such as Tor, to access. Onion sites, or dark web websites, are sites on the dark web that can typically only be accessed using special software like the Tor browser.
Onion Links: How To Access Them
Such fake passports are used to facilitate illegal activities like human trafficking, drug smuggling from one nation to another, and illegitimate immigration. This activity of selling and purchasing fake passports undermines national security and poses a major threat to global safety. Another instance could be the individuals behind the 2015 attacks in Paris, who made use of fake passports to get a loan in advance for the attacks.

Bitcoin Services

If you make use of a password manager, then it may come with a feature that monitors the dark web for mentions of your email address and password, or any other personal details. It’s something built into the password management services offered by Apple and Google as well, so you don’t need to trawl through data leaks manually yourself. With all of that in mind, you need to tread carefully when browsing, in terms of the sites you visit and the other users you interact with. Bear in mind too that laws about freedom of speech and censorship vary from country to country, which is part of the reason the dark web exists in the first place. In the European Union, the General Data Protection Regulation (GDPR) has influenced how personal data is handled, including on the dark web. The GDPR imposes strict requirements on data controllers and processors, with substantial fines for non-compliance.
- Even though DuckDuckGo is the Tor browser’s default search engine, it doesn’t index dark web websites, which means you won’t be able to find .onion sites with it.
- These areas usually need specific darknet browsers such as Tor, which bounces the traffic through several layers or nodes to avoid the identification of IP addresses.
- They can be easily traced and even prosecuted if they share the information on the surface web.
- Incredibly disturbing things Spotlight documented included ads for the sale of human organs, murder-for-hire, even tickets to watch torture.
This will help you to remain anonymous and secure at all Tor entry and exit nodes. It uses TrustedServer technology on the entire server network to wipe out your data after every session. The Tor browser allows you to browse the internet anonymously and visit inaccessible sites. Today, many organizations exist that are created only to handle these reports anonymously and effectively. They know how to process the information and get it to the correct law enforcement agencies internationally. While Tor offers anonymity on the dark web, your online activities leave breadcrumbs that can reveal your identity.
Despite the fact that it can be used for anonymity, freedom of speech, and journalism, the Dark Web is home to some of the worst internet scams. As a result, business entities should pay attention to the dark web and strengthen endpoint protection measures to mitigate risks. The surface web is the most familiar layer, comprising websites indexed by search engines like Google or Bing. This layer includes publicly accessible platforms such as news websites, e-commerce stores, and social media. Safety concerns on the dark web include encountering criminal-run websites offering illegal goods and services, with the added risk of exploitation and theft. Engaging in illicit activities can lead to prosecution, as the law applies equally in this hidden part of the internet.
What Is Tor?
The dark web allows users to gain access to illegal markets that may allow them to improve their quality of life. For instance, day-after pills are illegal in several conservative countries that consider abortion illegal but are accessible on such markets (the same markets that also sell street drugs). One must ensure that encryption tools like PGP (Pretty Good Privacy) are used for safe connection. Further, it is crucial to ensure that all transactions are conducted on encrypted and secure platforms to avoid being tracked and prevent malware issues. Some individuals access the dark web to share sensitive information or leak documents without actually revealing their true identity. Several platforms (one of them being SecureDrop) allow whistleblowers to pass on sensitive information securely, to journalists.