Avast SecureLine VPN encrypts all of your internet traffic to help block hackers and keep snoops out. Install Avast SecureLine VPN today to browse safely and securely, wherever your online travels take you. A lot of illegal activity occurs on the dark web, and onion websites are popular hangouts for cybercriminals and scammers. But if you use antivirus software, avoid clicking shady links, and stick to known sites you should be okay.
The provider also offers a dedicated CyberSec suite that prevents annoying ads and blocks malware and trackers. A reliable, fast, and user-friendly VPN service offering lots of customizable options for privacy geeks. You should never use your personal information on the dark web anywhere else in your life.
Bitcoin – New Links (

When you’re done surfing or shopping on the dark web, don’t forget to shut down Tails. The major advantage of using a live OS such as Tails is that, on shut down, the OS wipes itself from the thumb drive you’ve installed it. In terms of functionality, I don’t think there are too many differences between regular IMAP, POP3, and SMT services and the stuff you can use to communicate on the dark web. You should stay away from everything labeled “porn”, “card skimming services”, “PayPal hacks”, “firearms”, “real fake IDs and passports”. Believe me – there are plenty to go around and each and every one of them are being kept under surveillance. Not to mention the fact that you’ll get exposed to some stuff that will definitely make you take several cold showers.
Many dark websites are set up by scammers, who constantly move around to avoid the wrath of their victims. Even commerce sites that may have existed for a year or more can suddenly disappear if the owners decide to cash in and flee with the escrow money they’re holding on behalf of customers. These groups develop their own sophisticated malware, sometimes combined with pre-existing tools, and distribute them through “affiliates”. Here are some things to keep in mind while browsing your favorite dark web websites.
- It also keeps the graphical copy and text of the page for better accuracy.
- Adamant offers blockchain-based secure messaging without needing phone numbers or email addresses.
- This article aims to shed light on the more constructive side of the dark web, guiding readers toward reputable resources and reliable information.
- Dark web search engines are an alternative to having high technical knowledge, something hackers, journalists, and security firms are used to.
- Founded around 1999 by activists in Seattle, it has since grown to over six million users worldwide.
How To Buy Credit Cards On Darknet?
It also keeps the graphical copy and text of the page for better accuracy. Launched in September 2022, Torzon Market operates on the Tor network and features over 11,600 illegal products, including drugs and hacking tools. It enhances buyer transparency by importing vendor feedback with PGP proof. Torzon offers a premium account option for additional benefits and is valued at approximately $15 million, accepting payments in Bitcoin (BTC) and Monero (XMR).
What Is The Purpose Of Using A VPN When Accessing The Dark Web?
This service protects messages from interception and censorship, critical for journalists and activists. Sigaint provides encrypted email favored by whistleblowers and privacy advocates, focusing on ease of use and robust security. For real-time messaging, Ricochet Refresh offers decentralized, peer-to-peer encrypted chats over Tor without central servers, greatly reducing surveillance risks. These services form the communication backbone for sensitive conversations in high-risk environments. Deep Search is an open-source dark web search engine designed to index and explore onion space, the hidden services within the Tor network. Known for its accuracy, Deep Search stands out by delivering precise and useful results, avoiding the spammy links commonly found on similar platforms.
MULTI-LAYERED ENCRYPTION
These high levels of anonymity increase the opportunity for the “bad guys” to sell drugs, stolen IDs, credit cards, weapons, and many more compromised products or information. Simply download the file, install the software, and you’re ready to use its web-based interface. Next, disable Javascript in your Tor browser to prevent malicious scripts from attacking your browser sessions. You can disable Javascript by clicking on “Preferences” in the macOS app or “Settings” in the Windows app.

Best Online Anonymous Apps Of 2025
If this sounds similar to The Wayback Machine, the concept is indeed the same. However, The Wayback Machine allows website owners to block their sites from being archived, while archive.today does not. In 2021, they showed how tax rates benefit the rich, and they relied on stolen or leaked IRS documents to do so.
FAQs On The Best Dark Web Search Engines
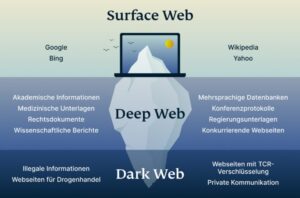
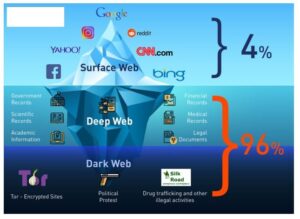
In contrast, sites hosted on the dark web can only be accessed via onion routing with Tor, or another dark web browser. AVG Secure VPN masks your IP address from other internet users, the websites you visit, and even government surveillance. And thanks to ultra-secure, end-to-end encryption, your online activity is obscured. Naturally, this makes the dark web a breeding ground for illegal activity. But onion sites can also serve nobler goals, like providing access to information and independent journalism in countries with government censorship.
What Is OnionLinkscom?

The best Tor sites are under constant threat of closure, including Tor directories like the Hidden Wiki, so having a backup in case one goes down is handy. Tor Search constantly crawls (onion) websites 24 hours a day, 7 days a week. In addition, it also revisits already indexed sites to update discover and remove downed and offline sites. However, to maintain the servers, they offer the possibility of inserting advertising banners on their home page. Tor Search is a very efficient search engine because it indexes new content all day from the TOR network.

Its philosophy emphasizes privacy and not registering user information. It’s not illegal per se to access an onion website, but that doesn’t mean your actions while connected to the dark web are immune from law enforcement. It’s still illegal to commit crimes while connected to Tor, regardless of whether or not you think you’ll be caught.
Stay Aware And Vigilant
That means that when Tor is compromised, or perhaps there’s a new vulnerability exploit in the Tor network, a VPN will still protect your privacy. The compromised Tor exploit might trace back to you, but then again, your VPN will lead it somewhere else – which makes it impossible to be traced back to you. It’s not a secret that ISPs (Internet Service Providers) and the FBI are tracking Tor users.
The Hidden Wiki is essentially a curated directory of .onion websites accessible only through the Tor network. It organizes links to a wide variety of dark web destinations, including popular marketplaces where users buy and sell goods anonymously. It also lists forums and communities where people share information, discuss darknet markets, and exchange security tips. It also connects users to hosting services and whistleblower platforms, facilitating secure communication and file sharing on the dark web. Our curated list of legitimate dark web sites above offers a safe entry point for first-time explorers. Unlike standard web addresses ending in .com or .org, .onion links represent hidden services, meaning they cannot be reached using regular browsers or search engines.