Because VPNs offer users anonymity and mask their actual location, they’re also effective tools for accessing geo-locked services. VPN stands for virtual private network, and it acts as a security bubble for communications from your device. A VPN automatically encrypts your data as soon as it leaves your device through the VPN server. This means your private information, location, and any communications you send are hidden and protected. The first rule for accessing the dark web is to go into it with a purpose or a defined goal.
Be Cautious Of Links
Still, there are plenty of good reasons to access it, like research, whistleblowing, journalism, and financial privacy. Within the dark web, there are various hidden websites, known as darknet markets, where illicit goods and services are bought and sold. These can include drugs, weapons, stolen data, and even hacking services. It is important to note, however, that not all activities on the dark web are illegal. Many individuals use it to communicate securely and anonymously or to access information that may be restricted or censored in their countries. However, while visiting the dark web itself isn’t against the law, engaging in illegal activities there is.

The Dark Web’s cornerstone is built upon specialized anonymity networks and protocols that allow users to access hidden services without directly revealing their identity or location. Understanding the differences and capabilities of various anonymity tools will help you make informed decisions about which networks best serve your needs. A VPN encrypts your web traffic to ensure it’s hidden from the big brother who could be watching you online. I2P is a private network built for secure, anonymous communication. Instead of the onion routing Tor uses, I2P relies on unidirectional tunnels and garlic routing, which bundles multiple messages together for better traffic obfuscation. It uses its own internal DNS to access “eepsites”, not .onion addresses.
In-Depth Guide On How To Download Instagram Videos Beginner-Friendly
Although the social application is known for collecting data on its platform, it does not like sharing the information with others. It will offer you an additional layer of encryption to access the deep parts of the internet. The dark web is a part of the internet that you only step into with a specific tool (Tor, more on this later in the article).
Which Is The Best Free VPN For Tor?
The best Android option is the Tor Browser, available on Google Play. For added privacy, use Orbot, which enables system-wide Tor routing for other apps. However, you won’t be able to use I2P to access as many official dark web sites as Tor. IP2 is faster than Tor and offers stronger peer-to-peer security, as it uses one-way tunnels to encrypt traffic — meaning, only inbound or outbound traffic could be intercepted, not both. In addition, it uses a distributed network database which is harder to attack than Tor’s fixed, trusted Directory servers.
Best Dark Web Sites 2025 – Detailed List
Our expert industry analysis and practical solutions help you make better buying decisions and get more from technology. Tor2Web is a rather popular proxy that works with the Tor network. All you have to do is replace “.onion” at the end of the onion URL with “.onion.to”, “.onion.city”, “.onion.cab”, or “.onion.direct” and you should be good to go. The US government created the dark web to help its spies communicate and exchange information securely. The Onion Router (Tor) also made the technology available in 2002.
Taking the necessary precautions makes tracing your activities on the dark web difficult. Although the Tor browser has sufficient encryption, combining it with a VPN offers better protection. However, you should not see it as an opportunity to engage in illegal activities to avoid trouble with authorities. This will help you to remain anonymous and secure at all Tor entry and exit nodes.

Of course, this sort of site poses no risk to legitimate dark web users, but it’s worth knowing that your usage of the dark web in general might draw attention to you. H25.io is a premium directory in the Tor network, offering access to a diverse and meticulously curated list of onion sites. Our mission is to simplify navigation in the complex and evolving world of the darknet. Here, you’ll find links to various resources, including educational archives, private forums, anonymous services, and more. Many people use Tor to avoid surveillance by government agencies, ISPs, or other entities monitoring online activities.
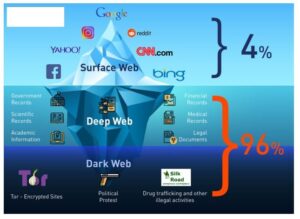
- It forms a small part of the Deep Web, a term that encompasses all parts of the internet that are not indexed by traditional search engines.
- If you must use one, ensure it’s a VPN with a strict, independently audited no-logs policy.
- There are different levels of security in the browser that are worth considering.
- Feel free to grab its 49% discount thanks to 3 free months for the annual plan.
- You might visit the dark web seeking anonymity or unique services, but this anonymity also attracts scammers.
Watch Out; Your ISP Could See You Using The Tor
TAILS (The Amnesic Incognito Live System) is a portable OS that runs from a USB or DVD, leaving no trace on your device. It forces all connections through Tor by default, ensuring complete anonymity while automatically deleting all activity upon shutdown. The dark web is the third layer of the internet and the hardest to find.
How To Access Onion Sites Without Tor Browser

They use a scramble naming structure that combines a string of letters and numbers to create URLs that are impossible to remember. No matter what you do online, there’s always at least some risk of being tracked — especially on the dark web. While no method guarantees complete anonymity, you can minimize the chances of being tracked with the right precautions. While there are other options, these are the only browsers officially recommended by the Tor Project. Using a different browser than these could put your privacy at serious risk and could expose you to attacks from cybercriminals.

Some of the deep web sites do not use standard top-level domains (TLD) such as .gov, .com, .net, etc. Other sites explicitly block search engines from identifying them. These sites are a hybrid tutorial-underground where wannabe hackers ask questions and professionals sell their services or stolen data. Keep in mind that you’ve to use very specific keywords when searching.
Sending Group Texts On Pixel 6: The Definitive Guide
- These sites bypass copyright protection and may be accessed only on the Dark Web to avoid legal scrutiny.
- Meanwhile, Facebook also offers dark web access to their social network.
- No matter what you do online, there’s always at least some risk of being tracked — especially on the dark web.
- Fake marketplaces and scams thrive on the dark web because there’s no one to turn to if you get scammed.
- This scale is why newspapers and mainstream news outlets regularly trot out scare stories about ’90 percent of the internet’ consisting of the Dark Web.
- Cryptocurrency enables buyers and sellers to exchange goods and services without revealing their identities, making it ideal for illegal activities.
However, there is an easy-to-use way around that, which we’ll talk about later. Just because the dark web feels anonymous doesn’t mean it’s invisible—especially to U.S. authorities. Schedule a demo to see how Cyble can protect your brand from dark web threats. The internet is huge—even in its shadows—it is possible to wander legally there. Research of the dark web is legal as long as national or international laws are not broken. Upon selecting the button for your operating system, you will be prompted to download the installer, which you should save to a folder.
The risk of being a visitor to this content could lead to being placed on a watchlist or immediate targeting for a jail sentence. The threats of online browsing can extend into the unplugged world if your computer or network connection can be exploited. Anonymity is powerful with Tor and the framework of the dark web, but it is not infallible. Any online activity can carry breadcrumbs to your identity if someone digs far enough. At the dark end of the web, you’ll find the more hazardous content and activity. Tor websites are located at this far end of the deep web, which are deemed the “dark web” and are only accessible by an anonymous browser.
If you are looking to read combating crime on the dark web online, many resources and platforms are available that shed light on the ongoing efforts to curb the growing threats of cybercrime. There are numerous phishing sites, too, as explained earlier, designed to fool users into giving up their personal data. Many cybersecurity and tech experts recommend using a VPN whenever you want to access the dark web via the Tor Browser or any other specialist browser. A quality VPN like ExpressVPN will encrypt your internet traffic and mask your IP address, providing an extra layer of anonymity when establishing the initial Tor connection.