This virtual bookstore is one of the oldest search engines on the internet. It was created by “Tim Berners-Lee”, who was also the creator of HTML and the Web itself. However, unlike commercial search engines, This is run by a confederation of volunteers. Not Evil is a reflection of what the community is looking for and what the community reports as abusive or inappropriate content. DuckDuckGo works in association with Yahoo, this association allowed it to incorporate search filtering based on dates and, in addition, in the results of a site show links that facilitate access to its subsections. The search engine provides several special features beyond the original word.

Dark Web Links For Financial Services
Yet, a user can utilise these search engines to locate other search engines and ultimately locate CSAM through the latter. Even if search engines block sites that directly share CSAM, it is still possible to find other entry points for onion sites that provide links to CSAM websites. With any major Tor website entrypoint, search engine, or link directory, a Tor user is only a few clicks away from CSAM content. Finding victims depicted in child sexual abuse materials is already a “needle in a haystack problem,” Rebecca Portnoff, the director of data science at the nonprofit child-safety group Thorn, told the Post. Now, law enforcement will be further delayed in investigations by efforts to determine if materials are real or not.

Tips To Stay Safe When Using The Dark Web
Langford explains that while the majority of these sites are legitimate places for people to upload legal images and videos, they don’t have the right checks in place. “The first thing is to engage and accept there’s an issue on their platform,” he says. But despite an increase in productivity and the availability of new tools and technology, the IWF’s humble resources remain overwhelmed by the sheer scale of the task it faces. Of the 105,047 URLs flagged for removal by the IWF’s 13 analysts, 82 per cent were from image hosting websites.
Dark Web Links For Email Services
Thus, staying connected to a VPN when you access these sites is vital. Dark.fail is an easy-to-use .onion platform equipped with a status checker that tracks website uptime. The site offers access to PGP-verified URLs and runs free of JavaScript or tracking.
How The World’s Biggest Dark Web Platform Spreads Child Sex Abuse Material — And Why It’s Hard To Stop
Inactive members can usually regain full membership status by starting to comply, for example, by regularly interacting with other members through forum posts. Much like a regular business, the typical darknet CSAM forum is hierarchically organized, and different forum roles are distinguished (see Fig. 4; van der Bruggen and Blokland 2021b). He said his site was moderated and that his team did block users who “appear to be under 13”. “He was asking her to shake her bum, take off her top and trousers, which she thankfully did not do.”
- OnionShare is one of the best tools for that purpose, whether on the surface or deep web.
- For example, Whonix’s virtual workstation machine connects to the internal virtual LAN.
- But on Wednesday, officials revealed that 337 suspected users had been arrested across 38 countries.
- In addition, Darknetlive has a list of dark web vendors, which is very convenient — it offers detailed information about each vendor, including .onion addresses (in alphabetical order) and FAQs.
- Home Internet connections and faster upload and download speeds have enabled a technology-driven revolution in the lifestyles of modern society.
Over the past three years, the site amassed around 1.8 million users worldwide. It hosted approximately 91,000 unique videos, amounting to nearly 6,288 hours of explicit content—all shared on a highly profitable network. He says gaining access to those darkest sites on the platform is not easy. The sellers are wary of being infiltrated by law enforcement, so don’t let just anyone in. The dark web is often confused with the deep web, but they are not the same. The deep web, also known as the invisible web or hidden web, is simply every web page not indexed by standard search engines.
Onion Links: How To Access Them

This number is terrifying in its sheer volume and speaks more to how pervasive CSAM is on the platform rather than being any indicator of proactive action on Telegram’s part. Even more disturbing is the fact that this massive tally represents entire channels and does not reflect the number of individual instances of CSAM that were found or reported on Telegram. It’s also important to note that because Telegram does not implement any proactive moderation or detection tools, and refuses to moderate anything except publicly accessible content, these reports are primarily from individual users. Furthermore, it is unclear if Telegram ever reports instances of CSAM to law enforcement or proper authorities. Members gained access by sharing such videos and livestreams of the minors they had coerced, as well as videos of adults abusing minors. And not just Telegram’s own users – but the untold numbers of people being abused and exploited on and through the app without their knowledge, the countless families and communities devastated because of the crimes the app enables.
- If you’re new to the deep/dark web, DuckDuckGo’s onion link should be your first port of call.
- Both recirculated and new images occupy all corners of the internet, including a range of platforms as diverse as Facebook Messenger, Microsoft’s Bing search engine and the storage service Dropbox.
- Users can explore onion sites easily and search for content without having to know any specific onion links in advance.
- This ensures greater security and privacy, making it much more difficult for snoopers to get in.
- And most importantly, be patient as you’ve to sort through a lot of useless results.
OnionShare
The website has an advanced search filter and an easy-to-use interface, which makes it easy to find what someone is looking for. Whether local or international goods, research documents, banned drugs, you name it, everything is available on this dark web platform (that’s one of the reasons why this should be monitored for security purposes). You can choose the best darknet (.onion) website that suits you and start surfing. For safer browsing, it is highly recommended to also use a VPN and antivirus software.
It’s great how the site has a Security Scenarios section too, where it offers personalized security tips for specific audiences (activists, academic researchers, journalists, and more). SecureDrop is an open-source submission system that nonprofit organizations (NGOs), journalists, and news organizations can use to share and receive sensitive files securely. It’s used by 50+ news organizations, including ABC, Bloomberg News, CBC, and The New York Times. Darknetlive contains articles about everything related to the dark web. Articles are published regularly and include interesting information, images, and quotes from officials. This way, if you’re interested in a specific topic, you can find it quickly.
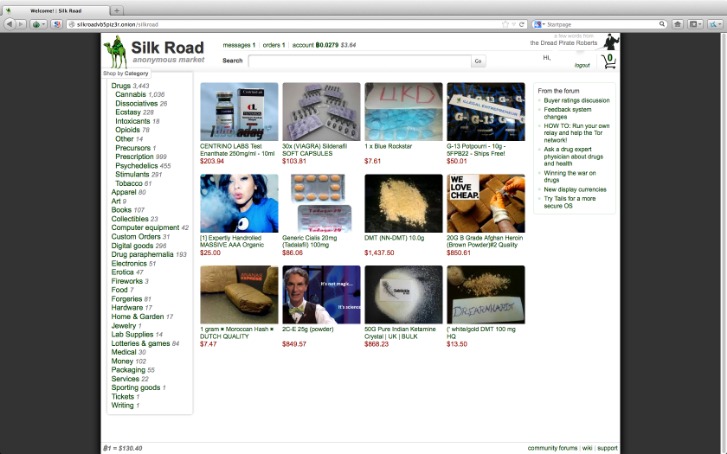
Like social network sites in the clearnet, darknet CSAM forum members maintain profiles and are known to other users by their nicknames. Forum members may communicate with each other not only in discussions and in private messaging but also by liking each other’s posts or the contents of the media sections. Infamous HSes marketplaces like Silk Road and Alphabay serve hundreds of thousands of online customers. They mirror the workings of legal marketplaces on the clearnet, such as Ebay, and facilitate vendors in advertising their product and offer escrow services to customers paying for their purchases in Bitcoin or other crypto currencies. Many marketplaces also have chat forums that vendors and customers alike use to introduce themselves and their products, review their experiences, and provide feedback and tutelage to others in the online community. In 2020, the IWF said analysts actioned 68,000 reports which were tagged as including “self-generated” child sexual abuse content – a 77% increase on the previous year.
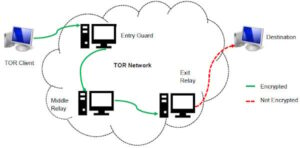
To explore it, you need to install Tor and use a dark web search engine or directory to find and visit onion search engine links. As hoped, the Tor anonymous network grew in popularity among computer enthusiasts, privacy advocates, journalists, dissidents under repressive governments, and others desirous of strict secrecy. At the same time, Tor became an effective shield for the illicit sale of heavily controlled goods, such as guns and drugs.
Child Sexual Abuse Material In The Digital Age
Tech companies, law enforcement agencies and legislators in Washington responded, committing to new measures meant to rein in the scourge. DARPA has since awarded Carnegie Mellon a three-year, $3.6-million contract to enhance Traffic Jam’s basic search capabilities as part of Memex, with machine-learning algorithms that can analyze results in depth, according to the university. Schneider is the project’s principal investigator and a research professor in the Auton Lab at the university’s School of Computer Science, which studies statistical data mining. Furniture in a hotel room, for example, could help law enforcement identify the location of trafficking operations.
Videos By VICE
The authors would like to thank the unnamed police force who collaborated with them in the production and delivery of this research project. Different combinations of moves suggest there’s no one “type” of newbie offender; they approach the community for a range of reasons and use different tactics in the process. Even the self-imposed label “newbie” positions them not as outsiders looking in, but as already part of the community, albeit in a low-status role. Aside from explicit statements about being new to the community, they often do this by stating that they lack offending experience. Expressing appreciation This group of offenders show their appreciation of individual members and the community as a whole.
Organisation alerts users who conduct CSAM searches of the illegality of their actions and directs them to help resources21. As early as 2011, research revealed the widespread distribution of CSAM in peer-to-peer networks15. This issue affects not only Tor but also the I2P and Freenet anonymity networks; in a 2022 investigation, a Freenet content analysis revealed that 12.0% of the 7161 analysed freesites contained CSAM16. The first systematic analysis in 2013 indicated that 17.6% (206 of 1171) of the onion services surveyed shared CSAM and concluded ‘The support for the further development of Tor hidden services should hence stop1’.