Keybase is an exciting identity service that aims to make it easy for you to link the presence of your online identities together in a cryptographic way. You can upload your PGP key or have the site create one for you, and use it to cryptographically link your Twitter profile, Github account, or Bitcoin address together. The process costs a fee, but unlike other “tumbler” or “mixing” services, there is no risk that Wasabi or any of its users could scam you out of your coins. One of the most popular ways to get around the dark web is not to use a search engine at all.

Can You Be Traced On Tor?
If a drug checking service knows where a substance came from, they can decide whether it’s more appropriate to share any alarming results locally or online. In Barratt’s eyes, these far-from-straightforward results underscore the importance of expanding drug checking services. When you can’t necessarily count on cryptomarkets offering a safer supply, local drug checking becomes even more essential. The researchers focused on the five most common drugs sent in for testing—MDMA, cocaine, amphetamine, methamphetamine and LSD—to ensure that there would be enough data points to produce reliable results in each case.
- Furthermore, data will help to detect attacks against the network and possible censorship events.
- Today, strangers may contact you on social media offering drugs to buy.
- Vendors are also critiqued, and many of them have myriad reviews.
- Many social media platforms keep their presence on the dark web, and it is no surprise that Facebook has a .onion portal.
- Its affordability and reliability have earned it a loyal customer base.
The goal of an anonymous and privacy network, Tor, is not to engage in the extensive collection of data. However, data is required for understanding, monitoring, and improving the network. Furthermore, data will help to detect attacks against the network and possible censorship events.
Tips To Stay Safe When Using The Dark Web
Unfortunately, others are fake and fraudulent websites that exploit the reputation of the dark web to con people. Moreover, malicious actors can attempt phishing scams to steal your data and identity for extortion. It is easily accessible by the general public and requires no special configuration. You can find sites like Facebook, Wikipedia, e-commerce sites, YouTube, and more here. These sites are a hybrid tutorial-underground where wannabe hackers ask questions and professionals sell their services or stolen data.
Science X Account
It is a relatively new provider but offers better features than most established VPNs. The provider also offers a dedicated CyberSec suite that prevents annoying ads and blocks malware and trackers. NordVPN is one of the best VPNs to combine with the Tor browser whenever you want to surf dark sites. It offers top-of-the-line security and fast speeds for a smooth browsing experience on the dark web. ActiveX and Java frameworks are susceptible to being exploited by hackers. Since you are navigating in uncharted territories with all the myriad threats today, you’ll have to disable them in your network settings to stay safe.
Operations

The dark web marketplaces are mainly defined into two categories. Telegram channels supplement traditional onion sites, blurring lines between the dark web sites and more mainstream communication tools. So, it’s only natural to find ways to keep in touch with your darknet buddies and/or customers.
- A VPN like Surfshark encrypts your internet connection and makes it harder for others to see your real IP address.
- Sci-Hub gives access to millions of scientific papers, mostly ones from behind paywalls.
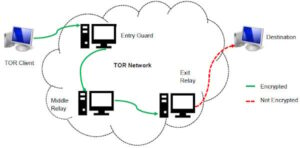
- The three nodes separate your IP address from your destination and enable two individuals to communicate without either party, or any middleman, knowing who the other is.
- By approaching this hidden corner of the internet with informed caution and ethical awareness, you can navigate it more safely and responsibly.
- Unlike other search engines, it does not collect or share web activities and personal data of users.
- Avoid using payment methods that can easily expose your identity.
Report It To The Authorities (if It’s Safe To Do So)
Instead, they are designed using a cryptographic key and can be accessed only through software like the Tor browser. Also, you can set a strong password to protect your message and choose how long it will take to expire. This is the best place to get short and reliable links to an unalterable record of any webpage across government and corporate websites. The Tor Metrics is a good place to get more information about the Tor project.
FAQ: More About Onion Sites
Contrary to popular belief, making a loved one become abstinent (even if you can) won’t cure the underlying issues that may have led them to use in the first place. For people who use opioids, it also increases their risk of overdose when they resume use with lower tolerance. My sources agree that unwanted fentanyl is found in lower levels in drugs bought online compared with street drugs. Vendors with higher feedback ratings can get away with asking for “early finalization.” This system (along with the reviews and forums) incentivizes them to sell what they say they’re selling; ripping people off has consequences.
Onion Links: How To Access Them
That’s helpful because Tor can suffer IP leaks and malicious actors can run Tor servers. Basically, if a Tor IP leak occurs before you connect to the VPN, your real IP address will be exposed. But if you connect to the VPN before connecting to Tor and an IP leak occurs, only the VPN’s IP address will be exposed. For example, there are separate categories for blogs, email services, file uploaders, forums, and more. I tested all the website links on The Hidden Wiki and almost all of them work (I was able to access sites like Deep Web Radio and ProPublica without any issues).
You can also take a look at the blogs & essays section if you want to find some nifty coding resources. Well, VPN over Tor is basically its opposite – instead of going through the VPN first, the signal passes through the Tor network, before going through the VPN. By using Tor, and especially in combination with a VPN, your internet signal is encrypted, making it invisible to your ISP. The Dark Web is a hidden part of the internet, completely different from the clear web we all use daily.
No, it isn’t illegal to browse the dark web, and there’s nothing inherently wrong with visiting a Tor website. Stay private with a tool like Surfshark’s Alternative ID to mask your contact details and use generated data on sites you don’t trust. ZeroBin is an attractive option for anyone looking to share sensitive information without compromising privacy.

As a result, it not only focuses on the UK but also provides worldwide news. It will offer you an additional layer of encryption to access the deep parts of the internet. The dark web is a part of the internet that you only step into with a specific tool (Tor, more on this later in the article).