Just like when navigating the surface web, the dark web has similar risks that should be taken into account when protecting your personal information. But you can face criminal charges if you use the dark web to sell or purchase illegal firearms, drugs, pornography, stolen passwords, hacked credit card account numbers, or other items. For example, dissidents who fear political prosecution from their governments might use the dark web to communicate with each other. As many as 70.79% of users claim to use the Tor browser for anonymity, 62.28% said they use it for additional security, and 27.07% used it out of curiosity about the dark web.
Avoid Downloading Dark Web Files
Torrenters can also make use of port forwarding, which allows connections to more peers in a torrent swarm. The former protects traffic using AES-256-GCM encryption and 4096-bit RSA certificates with SHA512 for server authentication. The latter uses ChaCha20 for symmetric encryption, which is authenticated with Poly1305. Nevertheless, Proton VPN says that the situation is different for VPNs. “Within the current Swiss legal framework,” it says, “Proton VPN does not have forced logging obligations.” It goes on to recommend the use of a VPN or Tor connection when using its email client. In any case, it can be used for any dark web activity thanks to various privacy features.
Never Download Files
In this guide, we’ll explain what the dark web is, how to access it safely, and why using a VPN (Virtual Private Network) with Tor is essential for anonymity. Freelancing alongside these roles, his work has appeared in publications such as Vice, Metro, Tablet and New Internationalist, as well as The Week’s online edition. Remember to uninstall any plug-ins you have before downloading, or prepare for them to be blocked – they can sometimes reveal your IP address, even if you’re using a VPN or onion router. Importantly, each node is representative of an additional layer of encryption. No node can track the complete path the traffic has taken, and more importantly, neither can anyone who finds it on the other side. Only the entry node can view your IP address (more on how to stop this happening later).
Legal Uses Of The Dark Web

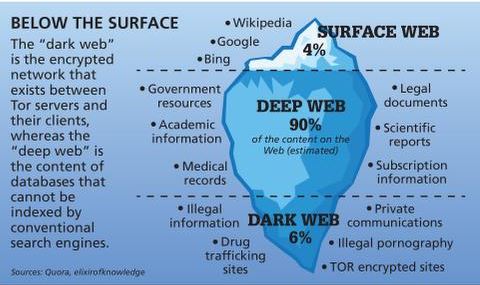
The dark web is a small subsection of the deep web that’s only accessible with special tools, software or authorization. Similar to the deep web, search engines don’t index material that’s on the dark web. What’s more, law enforcement agencies monitor dark web activities. Accidentally downloading or viewing illegal materials may result in severe legal consequences. Security solutions like anti-virus software protect your system and network from malware and other threats.
Best Free VPNs For The Dark Web: Safer Access
Other options are the Freenet and I2P (Invisible Internet Project) peer-to-peer networks, both of which provide censorship-free communications. The dark web is a refuge for information leakers and whistleblowers. The dark web is the perfect avenue for communicating and publishing sensitive information with no fear of retribution, such as imprisonment. VPN Over Tor is when you first connect to the Tor network and then connect to your VPN.
- However, its network is still small, and there aren’t many hidden services available yet.
- Hence, you’ll see accurate search results similar to searching on Google.
- To say the least, DOT Security does not recommend going to the dark web unless absolutely necessary.
- Since you are navigating in uncharted territories with all the myriad threats today, you’ll have to disable them in your network settings to stay safe.
- Since .onion URLs can be complex and random, consider bookmarking reliable sites in Tor for easier access.
- Sites often have simple black or dark-themed backgrounds and minimal design elements.
The Legal Aspects Of Dark Web Browsing

Though the dark web offers anonymity for journalists and activists in oppressive regimes, it raises many ethical concerns. You can use these dark web investigation tools to check if your company’s data is available on the dark web. Tor, I2P, and Freenet are three common technologies that make up the dark web.

Why Use Tor For Accessing The Dark Web?
The surface web and the deep web make up between 94-95% of the entire internet. Originally used by the United States Department of Defense for anonymous communication, the dark web is now a place for those wishing to stay anonymous themselves. To say the least, DOT Security does not recommend going to the dark web unless absolutely necessary. However, if you’re going to venture into the dark web, you’ll need to be well–prepared, so keep reading to keep safe.
However, you should not see it as an opportunity to engage in illegal activities to avoid trouble with authorities. Surfshark supports unlimited simultaneous connections to protect as many devices as possible. Also, try its services risk-free with the 30-day money-back guarantee. Lastly, the dark web is the portion of the deep web that is generally inaccessible and is much larger than the surface web. It relies on P2P connections and requires specialized tools and software. Tor and I2P are the two commonly used tools for accessing the dark web to provide anonymity.
On the dark web, traffic is routed through multiple server nodes that don’t log activity, obscuring the user’s origin and enabling anonymous communication. Onion sites, or dark web websites, are sites on the dark web that can typically only be accessed using special software like the Tor browser. These sites use “.onion” domains, which are made up of random letters and numbers up to 56 characters long. Dark web websites won’t show up on Google, but they are indexed by dark web search engines such as Torch. These search engines can help you discover .onion sites related to your interests.
Safely Browse And Verify Onion Sites
Surface web search engines can’t access the darknet, but specialized dark web search engines can help you find what you’re looking for. DuckDuckGo is a popular privacy-focused search engine that doesn’t track you across the web. DuckDuckGo’s dark web search engine may index pages on the dark web, but you’ll need to open it with Tor Browser. The quickest way to access the dark web is to download and install Tor Browser, which will route your traffic through the Tor network and let you access the dark web. On Tor, you can type in any URL you’d like to visit, including .onion links on the dark web.

What Is The Best VPN For Tor?
You don’t need special tools or a special browser like you need to access the dark web (more about that later). Anyone can access the deep web by using specialized search engines, dedicated web directories, and other sources that can help you find the data or information. The invisible web is made up of data and information that is not indexed and cannot be searched for by using traditional search engines. It includes media and archives which cannot be crawled and indexed with current search engine technology. Staying safe on the unregulated dark web requires vigilance, and its seedy reputation, fostered by controversy like that surrounding Silk Road, is well-earned.
Other users appreciate the browser as it allows them to circumvent censorship. And yes, unfortunately, those seeking to perform criminal acts also use it. Accessing the dark web requires more than just a standard web browser. Before downloading your dark web browser, though, there are a series of safety precautions you’re going to want to take first. These efforts could very well include accessing the dark web to help victims and hunt down criminals. This process, though, can often involve accessing the dark web for research into the most current malware on the market.
A VPN helps you browse the web more securely and privately by adding an extra layer of encryption to your data. However, not all VPNs are reliable, and some may collect your personal information while others slow you down. Keep in mind that in some regions like China and Russia, it’s illegal to use anonymizers.
The best thing is to actually understand how to find the fresh, new links. It has a feature called CoinJoin that combines multiple coins from different users into a single transaction. This makes it extremely difficult to find out who you are transacting with. Cryptocurrencies such as Bitcoin have been the dark web currency even before they became available to the general public.



