
This makes it a great option for watching videos from streaming services that are available only in other regions of the world. While the Tor Browser hides your online browsing, it only hides your online activity through the Tor Browser. If you need to protect or enhance your streaming, gaming, or torrenting activities, a Virtual Private Network (VPN) is a much better option as a secure connection to the net. As I mentioned previously, using the Tor Browser will slow down your browsing. Since your traffic goes through a series of relays, getting encrypted or decrypted along the way, things slow way down. This means Tor is a lousy option for streaming video, online gaming, or downloading files (torrenting).
Tor encrypts your traffic and routes it through multiple volunteer-operated relays, making it difficult to trace. Always use ethical judgment and stay informed about your local regulations. Malware, ransomware, and hacking tools are widely sold in underground forums.

Downloading And Installing TOR Browser

NordVPN has a huge worldwide network of RAM-only servers and high standards of both privacy and security. It makes visiting the dark web easy, with dedicated Onion Over VPN servers that connect you to the Tor network via the VPN. This negates the need to download, install, and run the Tor browser separately, and lets you access the Tor network without your ISP knowing.
- The Tor browser conceals IP addresses and browsing activity by redirecting web traffic through a series of proxy servers operated by thousands of volunteers across the globe.
- Alternatively, Linux distributions like Qubes OS provide advanced security features for those needing long-term privacy-focused computing.
- It’s a multiplatform problem-fixer that protects your entire digital life through a single app.
- That’s a trick question, because there isn’t even a good free VPN, much less a best VPN.
- Fake marketplaces and scams thrive on the dark web because there’s no one to turn to if you get scammed.
VPN Over Tor (Not The Best Option)
You can usually select the location you want to appear to originate from and VPNs will use a collection of servers and relays to make tracing your IP difficult. However, remaining anonymous can be invaluable to protesters, civil rights groups, journalists, lawyers, and other vulnerable groups. Illegal marketplaces are merely a small fraction of what’s actually there. Drugs, weapons, and stolen IP and data are all hot businesses on the dark web, with terabytes of information on offer.
VPNs And Proxies: Practical Alternatives
Good antivirus software (like Norton) helps detect and block these threats, providing an extra layer of security when accessing the dark web. I’ve put together detailed guides on how to access the dark web safely on both Android and iOS. I also share essential tips for staying secure there — personally, I always use a VPN for added privacy since Tor isn’t completely secure on its own. By being aware of the potential risks, following recommended security practices, and using the Dark Web responsibly, you can navigate this hidden part of the internet more safely and effectively.
Disable JavaScript & Use Privacy-preserving Tools

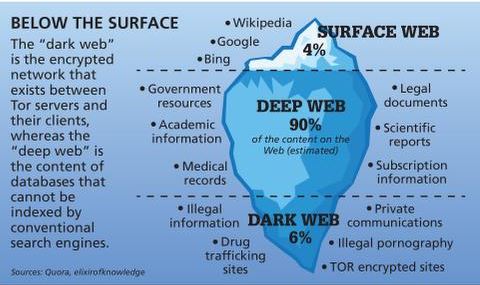
But the so-called “visible” Internet (aka surface web or open web) — sites that can be found using search engines like Google and Yahoo — is just the tip of the iceberg. The so-called surface web is readily accessible to all of us and thereby, less interesting. Well, relying on Tor to keep you anonymous online is a good recipe for disaster – we’ll see why soon.
Enterprise Network Design Mistakes To Avoid In 2025 Real-World Exam
If you choose to engage in legal transactions on the Dark Web, such as purchasing products or services, be cautious and carry out thorough research. Look for reputable forums or communities where users share their experiences and recommendations. Regularly update your operating system, web browser, antivirus software, and other applications to ensure they have the latest security patches.
Microsoft Word is one of the best word processors around, allowing you to craft powerful documents with an intuitive interface. If you know how to use Microsoft Word, you’re typically working with large files that span multiple pages. So, you’ll be happy to know there are several easy ways to delete a page in Word, including both blank pages and those you simply no longer need. The dark web has flourished thanks to bitcoin, the crypto-currency that enables two parties to conduct a trusted transaction without knowing each other’s identity.
US Cybersecurity Laws Related To The Dark Web
Anonymity doesn’t make carrying out illegal acts any more permissible, so be cautious about making purchases or downloading content. The Dark Web is a breeding ground for cybercrime, with many websites hosting malicious software, phishing scams, and other types of malware. Visiting untrustworthy websites or interacting with unverified sellers can put your personal data and financial security at risk. Cybercriminals often use the Dark Web to distribute ransomware, steal personal information, or commit fraud. The Surface Web is the portion of the internet that we interact with on a daily basis. It’s made up of websites indexed by search engines, such as Google, Yahoo, or Bing.
The Tor browser uses the Tor network, which was developed in the mid-1990s by US Naval Research Laboratory employees. The browser is open-source software that is free to download and enables anonymous communication online. Users’ internet traffic is sent through an encrypted network of volunteer-maintained relays around the world. Tor’s anonymity function is used by everyone from human rights workers and journalists through to drug and arms dealers.
Explore the legal nuances of accessing the dark web, including potential penalties and jurisdictional differences. The dark web’s hazards include many risks, related to network breaches or data compromises. These range from infections, unauthorized access, espionage, and phishing, to the theft of sensitive information like customer and financial data, intellectual property, and more. Each category carries risks of devaluing enterprises through reputational damage, disrupting operations via malware attacks, or defrauding companies through theft of critical information. Later, Tor’s underlying code was released under a free license, and a nonprofit called the Tor Project was formed.
Is It Illegal To Visit Dark Websites?
Similarly, researchers and cybersecurity professionals often use the dark web to monitor emerging threats, leaked credentials, or underground discussions that could signal potential cyberattacks. People in the United States and abroad can use it to venture into the dark web in privacy. With RAM-based servers in 90+ countries and features like WireGuard, IPv6 leak protection, and a kill switch, worries are over. For one, the VPN can’t see your online activities because of VPN encryption. We also prefer this method because of VPN’s all-encompassing security.
These sites can be used by both hackers and individuals looking to exploit vulnerabilities. These platforms sell counterfeit or forged documents, including passports, IDs, driver’s licenses, and other official papers. They cater to criminals or individuals seeking to commit identity fraud or avoid legal scrutiny.
- What should you do if your information is found in a data breach or you think it’s been leaked somewhere?
- At a minimum, users should ensure that their cybersecurity defenses are activated and up to date.
- It allows you to access and browse websites anonymously, using masked IP addresses.
- Read our comprehensive “what is the dark web” guide to understand how it works and the risks and benefits.
During this process, your ISP can still see that you’re using Tor because the entry node is now fully visible. Not to mention the entry node will see your IP address, so if it’s compromised, a hacker would be able to get a hold of it. More importantly, even the VPN service will now see what you’re doing inside Tor. Because of this, not many people are willing to give it a shot except if they have a very good reason.

Finally, many people consider the dark web a necessary tool for privacy and freedom of speech. In fact, there is an entire section of the dark web dedicated to pornographic content. However, it is important to note that not all of this content is legal. Freenet is still an experiment designed to resist denial-of-service attacks and censorship. Due to all the nodes that your traffic passes through, Tor by itself significantly limits bandwidth. Adding a VPN to it, even a fast one like IPVanish will make it even slower, so please be patient.



