There are often copious amounts of how-to articles, software exploits, and hacked credentials for sale. Not every visitor is a criminal, but this is where most cybercrimes begin. It has a feature called CoinJoin that combines multiple coins from different users into a single transaction. This makes it extremely difficult to find out who you are transacting with. This service is a good source of statistics if you have a school project requiring research on Tor and the dark web.

Stay Within Legal Boundaries
The Camouflage Mode is intended for people living in countries with heavy internet censorship, like China. It will make your VPN activities seem like normal traffic, so you can use an uncensored internet. However, this feature is only available on iOS, Android, and Windows.
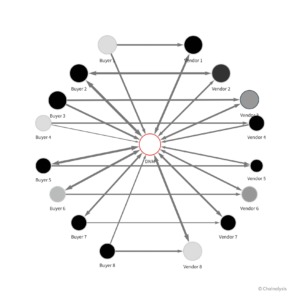
- Dark-web marketplaces operate through encrypted networks, primarily utilizing anonymity-enhancing technologies such as Tor (The Onion Router) and I2P (Invisible Internet Project).
- The categories are well organized, ranging from drugs and fraud to digital products, guides, and malware.What really sets it apart is its focus on security and usability.
- You can pay through Monera and Bitcoin using the escrow system or the traditional market account after making a purchase on this shop.
- Although these marketplaces are continuously shut down by law enforcement agencies, they still work today.
- As listed above in our article, even respected organizations like the BBC and ProPublica have a version of their site on the dark web.
How To Access onion Sites Safely
The only way to access the dark web is by using the correct browser and knowing the URLs of the pages you want to visit. Scroll on to learn more about dark web links (also called Tor links or onion sites), get the right links for some of the best Tor sites, and find out how to visit them safely. Kerberos is a darknet marketplace built with a strong emphasis on security, inspired by the legendary multi-headed guardian.
What Are Onion Sites?

All transactions use our secure escrow system, holding funds until you confirm delivery of your order. mark it means it has been verified as a scam service and it should be avoided. Monero’s ring signatures, stealth addresses, and RingCT ensure untraceable trades.|Serving 8,000+ users and 600+ vendors, it holds a 10% share of drug commerce—an emerging force since 2023. The dark web is part of the internet that is not indexed by standard search engines like Google, Yahoo, and Bing. It means you cannot access websites on the dark web with regular browsers like Firefox or Chrome. Instead, you need a specific configuration, software, or authorization, such as Tor, to access it.|The dark web is not easily accessible, especially with browsers like Chrome or Safari, as it requires specialized protocols like Tor’s onion routing. As a result, the recommended browser for accessing the dark web is the Tor (The Onion Router) browser. This is an estimated reading time to let you know how long it will take you to read all the content on this particular PrivacyRadar.com page. However, it has a sneak peek, easy guide steps, and/or a quick list providing quick in-page navigations and easily-found answers if desired. Yes, you can access the dark web on mobile — you just need the right app.}
ExpressVPN is an excellent choice for Tor and accessing the Dark Web. It has a proprietary onion site in the Tor network to give you safe access even if your country restricts VPN usage. The most interesting thing about NordVPN is its built-in Onion over VPN feature. It encrypts your traffic at the entry node and changes your IP address. This means you will get a VPN’s security and enjoy the anonymity of the Tor network simultaneously. We recommend you only visit safe dark web links to explore such as The CIA, Facebook, DuckDuckGo, and Torch.
Stay Safe On Dark Web Websites

This means you have to know someone who is already using the platform. Even without the code, you can visit the security section to get tips on improving your daily life privacy. The social media giant is also aware of the many attempts by repressive regimes to restrict its access.
Dark Web Marketplace Links
The BBC and other well-known news services are blocked in some parts of the world. But people can still access independent media via BBC Tor Mirror and similar dark web news portals. The BBC Tor Mirror is an international version of the BBC that focuses on world affairs, and it’s extremely useful for those who live under strict censorship laws. Deep web websites have to be hosted somewhere, and Impreza Hosting is one of those anonymous dark web hosting services. A host is basically a website’s house, or where it lives and takes up space. Impreza provides an affordable hidden space for black websites to base their operations.
In fact, create new throwaway accounts and documents if possible. Ensure you have used prepaid and unidentifiable credit cards when purchasing on the dark web. Avoid using payment methods that can easily expose your identity. Simply put, accessing and browsing the dark web is perfectly legal. For example, it maintains your privacy and enables you to access untraceable content and services.
Marketplaces For Everything Illegal
It’s not fancy, but it’s dependable, and that’s why I keep coming back. Incognito’s all about keeping things easy and safe—perfect if you’re avoiding street buys. What sets them apart is their support—real-time chat that’s saved my bacon a couple times when a deal went sideways.
Subscribe To The Blog Newsletter

However, if we’re being honest, the majority of activity on darknet markets involves illegal or heavily regulated items. A 2020 study found that almost 57% of sites on the Tor network hosted some form of illegal content. The site allows users to find and buy a vast variety of products and services. It’s known for its strong security features (like a trusted escrow system, PGP two-factor authentication) and anonymity. In fact, everything is in English, and the site picks up users everywhere in the world. People visit this market to buy stolen credit cards, personal data, remote desktop account credentials, and logs gathered from information-stealing malware.
For instance, after the closure of Genesis Market, its website came back after a few weeks. What’s more concerning is that most of the time, we don’t know about these flaws, and by the time we try to fix them, we come to know it’s too late. Like ransomware, criminals can buy software and inject your devices with viruses. With it, they can spy on people, steal their sensitive data, or secretly control their devices. These software are also capable of launching DDoS attacks and phishing campaigns.
However, this will likely lead to the rise of new, decentralized groups like RansomHub. Using a VPN, such as Forest VPN, in conjunction with the Tor browser can significantly enhance your privacy. The VPN encrypts your connection and masks your IP address, providing an extra layer of security.
They use pseudonymous wallets, privacy coins (like Monero), mixers, chain-hopping, and non-KYC platforms to obscure transaction trails.