
Because it doesn’t use a crawler or ranking algorithm, OnionLinks is static and highly dependent on manual submissions, which makes it unreliable for current or time-sensitive research. It filters content heavily and can be accessed both through the surface web (the traditional part of the internet) and the Tor browser. At a technical level, these engines access the dark web using specialized protocols, like the Tor project. Their crawlers run through the Tor network, allowing them to load .onion websites anonymously.
It contains a good selection of product listings that range over 35,000 items. The website has an interface and design similar to other dark web shops. It uses PGP encryption, two-factor authentication, and OPTP authentication to ensure users’ security.
ASAP Market
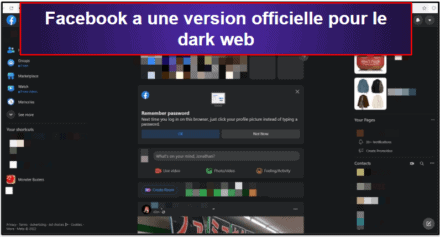
Although the Tor browser has sufficient encryption, combining it with a VPN offers better protection. However, you should not see it as an opportunity to engage in illegal activities to avoid trouble with authorities. Whereas the deep web is the part of the web not searchable by traditional search engines and requires special tools to access it. Also, you must log in or have a specific IP address or URL to access the deep web content. Many social media platforms keep their presence on the dark web, and it is no surprise that Facebook has a .onion portal. Facebook’s dark web version allows users to access the site where it is banned or restricted.
Top 10 Dark Web Markets
It’s also a playground for cybercriminals, illegal activities, and shady stuff. Its free plan comes with up to 1 GB of storage, 150 messages per day, and 1 email address. With rising online privacy concerns in the current digital age, the Tor network’s anonymity is becoming essential. It is a good way to prevent third parties from tracking online activities. People in countries with heavy internet censorship must get a VPN or Tor browser to access the surface web.
We have all heard the stories, so why not explore the Dark Web for yourself? If all this seems like a total minefield, find out how to get started, plus 14 of the best dark web websites to explore in 2025. Our commitment to delivering top – notch, engaging, and business – centric content is what sets us apart. We aim to be the go – to destination for industry – leading news, in – depth analysis, and practical advice. Navigating the vast expanse of the internet, the best Tor websites emerge as sanctuaries of privacy, security, and freedom. To access the Tor network and the best Tor websites, you’ll need the Tor Browser, which is specifically designed to navigate the Tor network.
How Did We Select These Best onion Sites?
While many search engines steer clear of the dark web’s seedier elements, Kilos embraces it and doesn’t filter search results. Tor Network, short for “The Onion Router”, is a network consisting of volunteer servers that encrypt Internet traffic and route it through multiple nodes. This technology makes it very difficult to track the identity or location of users. This is particularly useful for people living in countries with internet censorship, journalists, activists or simply for those who want to protect their privacy.

What Makes A Dark Web Market Different From Regular Online Stores?
It’s a type of support that facilitates the development of new techniques and skills. It’s known that the best place to purchase or even exchange various hacking tools is on the dark web discussion boards. In these forums, you can get stuff like malware, hacking tools, and exploits. They’re the tools that enable cybercriminals to conduct their attacks on businesses, institutions, and individuals.
Specifically, the I2P darknet is accessible, while the Tor network is accessible through the Orchid Outproxy Tor plugin. As listed above in our article, even respected organizations like the BBC and ProPublica have a version of their site on the dark web. No user names are tied to actual identities, and no moderation like one may find on Reddit.
As a user or cybersecurity professional, approaching these marketplaces demands utmost caution, thorough knowledge of operational security, and constant awareness of legal boundaries. Understanding both the benefits and dangers ensures safer interaction and more informed decision-making in an ever-changing digital environment. Although dark-web marketplaces utilize technologies like Tor and I2P to enhance anonymity, these methods are not foolproof. Law enforcement agencies continuously improve their ability to trace transactions and monitor marketplace activity. Abacus Market has emerged as one of the most reputable and widely used dark-web marketplaces in 2025.
Proliferation Of AV Evasion Tools (Cryptors)
These sites aren’t accessible via standard web browsers or search engines. Torch is one of the oldest and most reliable search engines on the Dark Web, with a database containing one of the largest indexes of .onion sites. As a result, you may see adult content, gambling, or other offensive websites during your searches, so be careful about the links you click.

Does Tor Hide Your IP Address?
Its affordability and reliability have earned it a loyal customer base. The platform’s activity has increased significantly over the past year, indicating its growing influence and market share in the underground economy. Overall, Abacus Market distinguishes itself through rigorous security measures, effective moderation policies, and a strong emphasis on protecting user privacy. Despite minor accessibility inconveniences, these strengths have solidified its position among the top dark-web marketplaces in 2025.
Without the right precautions, your IP address could be exposed, leaving you vulnerable to hacking, tracking, or even identity theft. Torzon Market has established itself as a significant player in the darknet ecosystem, offering a secure, user-centric platform for anonymous trading. Its commitment to privacy, diverse product offerings, and robust security measures make it a preferred choice for users seeking discreet transactions within the darknet. Established in 2019, Russian Market is a well-known and highly regarded data store on the dark web, specializing in the sale of PII and various forms of stolen data. Despite its name, the marketplace operates primarily in English and serves a global audience.
Methodology For Selecting The Best Dark Web VPNs
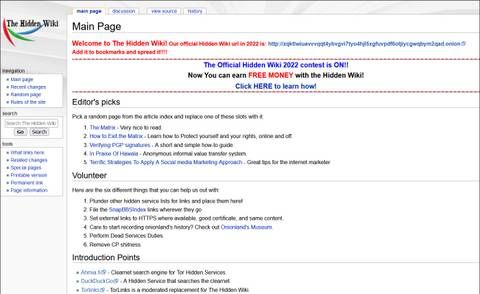
While it may have a reputation for seedy and dangerous content, many dark web websites are legitimate and useful resources. Keep reading for a rundown of the best dark links you might want to check out. While no approach guarantees complete safety, a careful and skeptical mindset serves as one of your most valuable tools on the hidden internet. Finding reliable sites on the dark web can feel like a guessing game—many onion addresses appear cryptic, and their ever-changing nature makes it challenging to build trust.
Exploitin: A Legacy Marketplace For Cybercriminals
- Dark web domains are generated in a cryptographically secure way, so they look like random strings of 16 characters or more (like 3g2upl4pq6kufc4m.onion, for example).
- Its emphasis on user anonymity and document forgery makes it a core tool for identity fraud.
- With its emphasis on user privacy and a diverse community that spans various interests, Galaxy2 redefines social interactions in the anonymous digital realm.
- Decrypting the data involves peeling back layer upon layer of encryption, hence the “onion” analogy.
- It’s particularly useful for sensitive communications that need to remain private.
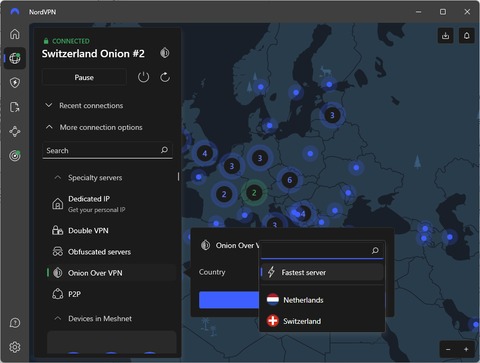
It enhances buyer transparency by importing vendor feedback with PGP proof. Torzon offers a premium account option for additional benefits and is valued at approximately $15 million, accepting payments in Bitcoin (BTC) and Monero (XMR). AVG Secure VPN encrypts your internet traffic and obscures your IP address every time you use it to go online — dark web or not. With a variety of server locations around the world to choose from, you’ll be able to navigate the web more privately and access the content you want. Onion sites are dark web sites that can only be reached through online routing via Tor, in which encrypted data passes through multiple nodes before reaching its destination.



