
Remember that illegal activities can still incriminate you, whether you are using a Tor browser. For example, you shouldn’t pirate copyrighted material, engage in terrorism, or share illegal pornography. The system is designed to provide enhanced security and privacy features. Its key features include kernel hardening, application firewall, package security, filesystem encryption, meta-proxy encryption, and binary integrity. Another essential security feature is that all incoming and outgoing data from the app is encrypted, including any private and public keys involved. Some of the deep web sites do not use standard top-level domains (TLD) such as .gov, .com, .net, etc.

Key Cyber Threats Facing The Financial Sector In 2025
In doing so, DarkOwl analysts uncovered a confluence between the three economies, indicating a possible interrelationship between the supply routes moving drugs, weapons, and people around the world. Sellers utilize various encryption tools to protect their communications and transactions from prying eyes. These tools allow traders to discuss weapon sales and negotiate terms without exposing their identities. Furthermore, encrypted communication platforms typically offer additional security features that augment the safety of transactions. To combat the illegal trade of weapons on the dark web, law enforcement is increasingly turning to advanced technologies.
It enhances buyer transparency by importing vendor feedback with PGP proof. Torzon offers a premium account option for additional benefits and is valued at approximately $15 million, accepting payments in Bitcoin (BTC) and Monero (XMR). Law enforcement agencies around the world are taking steps to combat the illegal sale of firearms on the dark web. In the United States, for example, the Bureau of Alcohol, Tobacco, Firearms and Explosives (ATF) has a dedicated dark web team that monitors online marketplaces for illegal firearm sales. The ATF also works closely with other law enforcement agencies, both domestically and internationally, to track down and prosecute those involved in the illegal sale of firearms.
A VPN encrypts the data traffic and keeps your activities private on the dark web. It also masks your IP address, making it difficult for government agencies to monitor or track your activities. We recommend using NordVPN as it offers top-notch security features, including dark web threat protection. WeTheNorth is a Canadian market established in 2021 that also serves international users. It offers counterfeit documents, financial fraud tools, hacking and malware services. It has an active forum and community along with an extensive user vetting process.
- These markets are often referred to as “darknet markets” or “cryptomarkets.” They are typically accessed through the Tor network, which provides users with anonymity and privacy.
- Investigators said those items were then sold to pawn shops around Orlando.
- Asaan had left his lap top on and police were able to access it and discovered he had searched on the Dark Web for firearms and conversations he had had with a number of sellers.
- They also mention their stealth practices to avoid detection, including that pistols are taken apart and hidden in power tools.
Imagine trusting a site where you’ve been buying or selling for months, and everything seems legit. Some marketplace operators first build trust by running a legitimate platform. Some sellers offer cracked versions of expensive software that you’d typically pay hundreds of dollars for. Others sell pirated eBooks, academic materials, and entire premium courses ripped straight from paid platforms. Unfortunately, the dark web hosts not only explicit but also deeply illegal and disturbing content.
- This veneer of legitimacy fuels further demand and normalizes the illegal trade.
- The US and Europe have seen an increase in nitazine-related overdose deaths in recent years, perhaps due to the halt in the heroin supply following the Taliban’s crackdown.
- Despite using a VPN, there’s always a risk of the VPN leaking your IP address through DNS or WebRTC leaks or misconfigurations when on a dark web forum or marketplace.
- It issued a press release revealing that, from December 2021, the website won’t be functional anymore.
- Doing so we have gained an understanding of what we can gain by monitoring the Darknet.
Easy Steps To Access Dark Web On Your Phone Safely In 2024
Listings aren’t public, but it’s steady—think drugs (weed, pills, some synthetics), a few digital extras like cracked accounts. They’ve got 2FA and encryption that’s tighter than a drum, which I’ve tested against crash-prone sites and found solid. Word’s out they’re going decentralized in 2025—less downtime, more trust, right in line with where things are headed.
The Full List Of Trusted Darknet Markets:
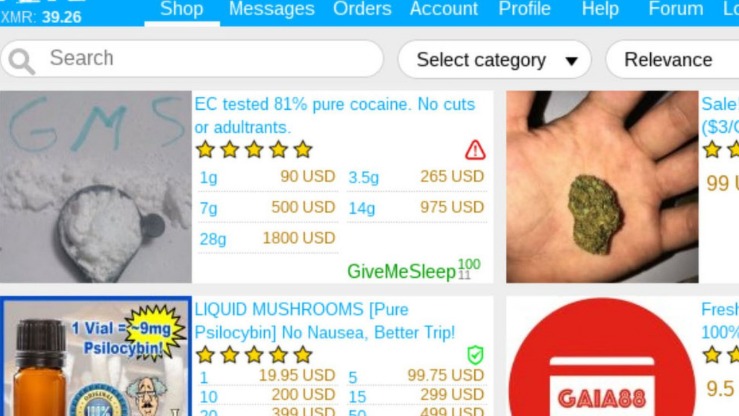
These markets sell a range of illegal goods and services, including drugs, weapons, stolen data, and counterfeit items, and they typically require special software like Tor for access. Nemesis Market is a relatively new wallet-less shop on dark web where you don’t need to deposit any amount in your wallet before buying products from here. The platform allows buyers to review the vendor’s products and services, so it’s easy for them to decide if the vendor is reputable or just scamming them.
Believe it or not, some dark web marketplaces have pretty advanced systems for building trust. Sellers often need to pay a deposit to prove they’re serious, and they build their reputation through positive reviews. In 2019, there were approximately 8,400 active sites on the dark web, selling thousands of products and services daily.
Abacus Market: Overview And Key Features
Deposits span from the hundreds to the tens of thousands of dollars, and the average deposit amount in 2024 was over $2,000. China-based Abacus vendors have many listings for research chemicals. They also sell PMK and BMK, which are precursors to MDMA and methamphetamine, respectively. His research further indicated that the majority of illicit small arms sold on the dark web—about 60 per cent—are shipped from the United States. Meanwhile, approximately 25 per cent of the armaments originate in Europe. Dr. Paoli said there is a dire need for new international cooperation to combat illicit arms sales made possible by the anonymity of the dark web.
How To Protect Your Identity While Browsing The Dark Web

It’s known for its strong security features (like a trusted escrow system, PGP two-factor authentication) and anonymity. From items like drugs, fake ID cards, and hacked bank accounts to more complex offerings like human trafficking, these sites carry all the illegal activities you can think of. Bohemia popped up post-Hydra takedown and brings a fresh vibe—drugs (weed, pills, some coke) and digital goodies like hacked logins, no exact listing count, but it’s growing fast. They take BTC and Monero, and the site’s got a sharp, modern look—vendor profiles are loaded with ratings and reviews, easy to skim. What’s dope is their forums—real talk, not just noise—building trust like Telegram’s side hustle vibe. Escrow’s standard, keeps things fair, and I’ve never seen it glitch out.
Darknet Threat Monitoring With KELA
Stick to cryptocurrency, avoid downloading anything, and don’t share any personal info. If you ever decide to explore the dark web, protecting your identity is crucial. Most people start by using the Tor Browser, which hides your IP address.
Additionally, you can opt for Subgraph OS as a second option to Tor. While accessing the dark web using Mozilla Firefox is possible, you must first adjust its settings. The only difference is that it passes your traffic through random nodes before reaching the destination. This means your activities cannot be traced or your browser history exposed. An easy way to find content on the dark web is to receive a link from someone who already knows about it.

What Exactly Is Sold On These Marketplaces?
Surfshark supports unlimited simultaneous connections to protect as many devices as possible. Also, try its services risk-free with the 30-day money-back guarantee. A budget-friendly VPN service allowing users to access dark web safely anytime, anywhere, and on any number of devices they want. A top-of-the-line VPN network that ensures maximum security while accessing dark sites online. The Tor browser allows you to browse the internet anonymously and visit inaccessible sites. Since the dark web is a hidden and uncontrolled part of the web, there is a high amount of malware infections present there.
It also has a message option to communicate with vendors or customers, users’ orders are tracked and there is a forum linked to this market. Onion sites aren’t really dangerous, but they could be when accessed through unfamiliar or suspicious links. The website has an advanced search filter and an easy-to-use interface, which makes it easy to find what someone is looking for.
Security And Anonymity Features
Also, you can set a strong password to protect your message and choose how long it will take to expire. The good news is that the platform will not see what you copy/paste. Your data is encrypted in the Tor browser before reaching the ZeroBin servers.



