Bear in mind too, that your internet provider will be able to see you connecting to Tor nodes, even if it doesn’t know exactly what you’re doing. Many people install a VPN as well, but then you’re putting your trust in an additional third party to not track your activities or report them to anyone else. Tor is like the public-facing door to the dark web, and there are even mobile apps for Android and iOS. To get on the dark web, you need a browser built for the job, and the best in the business is Tor. Tor is a browser engineered for extra security and privacy, and can be used to navigate the normal, surface web as well as the dark web.
- They engage in financial crime and sell other people’s stolen personal information, since they’re under the veil of anonymity.
- You risk legal consequences if caught participating in illegal transactions.
- Users who wish to gain access to such information are protected by the same anonymity the publishers of the content enjoy.
- It’s somewhere Google and Bing don’t index, and you need special tools to get to it.
Risks And Dangers
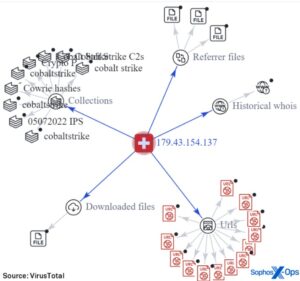
Even the smallest details about you can be useful to cybercriminals. That all is for general internet activities, you can guess how crucial having a VPN is when you hop onto something like the dark web. This explains how the market of the dark web marketplace is affected.
Find The onion Address You Want To Access
Avoid giving up real information, don’t log into your personal accounts, and don’t engage in conversations that could identify you. Downloading anything online can be dangerous, let alone the hidden internet. With the growing abilities of corporations to monitor and collect our data, the core principle upon which the dark web exists is now more relevant than ever.
Browsing The Dark Web

Counterfeiting businesses create fake versions of popular products and sell them on the dark web. Law enforcement agencies frequently target sites that distribute child pornography. For Example, In May 2021, authorities in Germany brought down Boystown, a child pornography network with more than 400,000 registered users.
Can You Be Tracked If You Use Tor With A VPN?

From choosing the right networks and privacy tools to avoiding scams and malicious software, every step you take should be guided by caution and informed judgment. Navigating the Dark Web can be a complex endeavor, but you don’t have to do it alone. Reputable organizations, security researchers, and privacy advocates provide a wealth of insights, tutorials, and software to help you explore safely and responsibly. Below are some trustworthy starting points and authoritative references. By keeping an eye on these alternative platforms and trends, you gain a deeper understanding of how privacy, anonymity, and underground markets adapt to new technologies and challenges. As digital ecosystems morph, staying informed and agile will help you make the most of evolving privacy tools—or avoid stepping into ever-more complex traps.
What Cybersecurity Surprises Does 2018 Hold?

Millions of customers’ personal data, including names, addresses, bank account and credit card account information, and many other forms of sensitive data. The core principle of the Tor network was first developed by U.S. Naval Research Laboratory mathematicians and computer scientists in the mid-1990s. The U.S. Army developed “onion routing” to protect intelligence communications online.

Official Security Advisories And Documentation
Dark-web marketplaces attract sophisticated cybercriminals adept at launching phishing scams, malware attacks, or ransomware threats. Buyers and sellers frequently face risks from malicious actors posing as legitimate vendors or customers, potentially leading to financial loss or exposure of sensitive personal information. Abacus Market has emerged as one of the most reputable and widely used dark-web marketplaces in 2025. Finally, product variety significantly influences marketplace choice.
- Monero and Bitcoin are two of the most commonly used digital currencies on the dark web markets.
- In most cases, the deep web exists to protect privacy, enforce intellectual‑property rights or comply with regulations.
- The dark web has no shortage of criminal activity, scams, phishing sites, suspicious links, and malware designed to trick newbies.
- Freebie VPNs will track their users’ online usage, as they make money by selling this tracking info to advertisers and other nosy parties.
Therefore, most cybersecurity experts recommend using Monero while shopping on darknet markets. If you think the Dark web marketplaces are just online shops, you’re wrong — these sites are the actual weapon stores for criminals. They provide criminals with access to everything they need, from launching attacks to stealing data, etc.
Dark net websites are called “Tor hidden services”, and they can be distinguished from normal websites by their URLs. Instead, download Tor, the most secure and user-friendly option for accessing .onion sites. Despite some skepticism about its origins and privacy due to its military development, Tor remains the preferred choice for safe dark web navigation. Darknets are not limited to criminal activities; nation-state actors use these hidden platforms for espionage, disseminating propaganda, and recruiting agents. The significance lies in the potential compromise of national security. Governments and businesses must invest in advanced threat intelligence, cyber defense, and counter-espionage measures.
Cybersecurity Best Practices For Protecting Your Digital Assets
There’s a significant risk to dark web users of being exposed to malware (malicious software) infections. There are several programs that hackers frequently use on the dark web. However, if you must buy items from the dark web, set up a secure, encrypted email with CounterMail or ProtonMail. For more information, read more about the most secure email service providers in my other post. Since you’ve now installed the Tor browser, you can safely browse dark web websites and other (previously) hidden websites. Then, simply click the operating system that you are using and download the file.
How To Remain Safe When Using Darknet Browsers
Its talent for keeping activity anonymous remains, but now protects malicious actors instead of innocent citizens of a given country. Then, a law enforcement agency (still unidentified) provided information to the FBI that later accessed the site’s host server. Deep down, the tip of the iceberg is where over 90% of the internet content is. As much as the dark web is supposed to promote free speech alongside bypassing censorship, many shady activities occur there. Removing your sensitive personal information from the dark web once it has been exposed is virtually impossible. This irreversible process highlights the importance of taking preventive measures by utilizing a service that monitors your data for potential breaches.
Open up Tor, and you won’t suddenly see the dark web staring back at you. Not only do you need a dark web browser, you need a dark web search engine too. This search engine will get you to the sites you need, though you can also go directly to dark web addresses if you know what they are, as with standard URLs.