
Indeed, Facebook, The New York Times and now even the CIA have sites on the dark web, hosting “onion” versions of their pages that can be accessed via the Tor browser. The spy agency is hoping to securely and anonymously collect tips, though its entire website, including job listings, are available on the onion service. Personal information, such as banking, social media, email accounts, and Social Security numbers may be up for sale on the dark web.
Are Sites On The Dark Web Illegal To Use And Visit?
The primary gateway to the dark web is the Tor browser, which stands for “The Onion Router.” Developed by the U.S. Navy and released to the public in 2004, Tor is favored for its unmatched security and privacy features. Unlike conventional browsers like Chrome or Firefox, Tor does not take the most direct path from your device to the web. Instead, it routes your connection through a series of encrypted servers, or nodes, to maintain anonymity for both users and websites. The dark web’s hazards include many risks, related to network breaches or data compromises. These range from infections, unauthorized access, espionage, and phishing, to the theft of sensitive information like customer and financial data, intellectual property, and more.
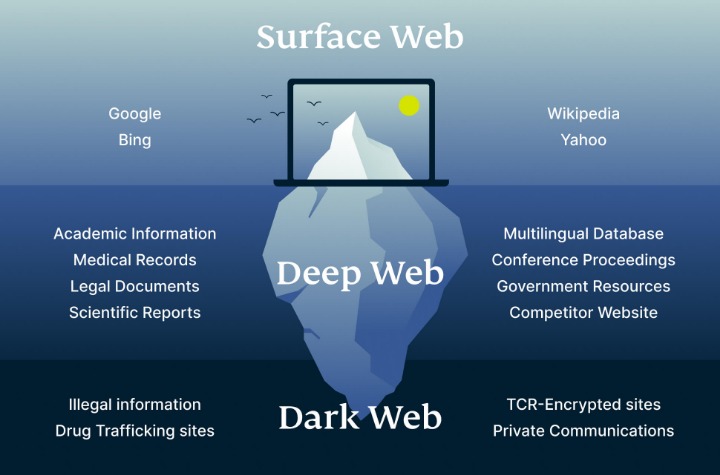
Myth 5: All Content On The Dark Web Is Easily Accessible
If you choose to visit the dark web, you must take the necessary measures to protect your privacy and security. The most common of these browsers is Tor, which launched in 2002 and serves millions of users. Another is the Invisible Internet Project (I2P), which specializes in the anonymous hosting of websites on the dark web. In darknet mode, you can select friends on the network and only connect and share dark web content with them. This enables individuals to form groups and only share content in a highly anonymous network of darknet users who they know.
How Does Personal Info End Up On The Dark Web?
The indie game Sad Satan was claimed to have been found via the dark web, but inconsistencies in the reporting cast doubt on the story. Ross Ulbricht, the creator of Silk Road, was arrested on suspicion of hiring a hitman to kill six people, but the charges were later dropped. People can contact assassins on the dark web who are ready to kill for money. Some folks have been cautious enough when browsing the dark web only to fumble at the last minute once they are done – they just get too lazy not to close everything. It means that it can be overwhelming to get what you’re looking for, and as a result, it’s very easy to stumble into a place you could never want to be.
How To Choose The Right Dark Web Monitoring Tools For Your Business?
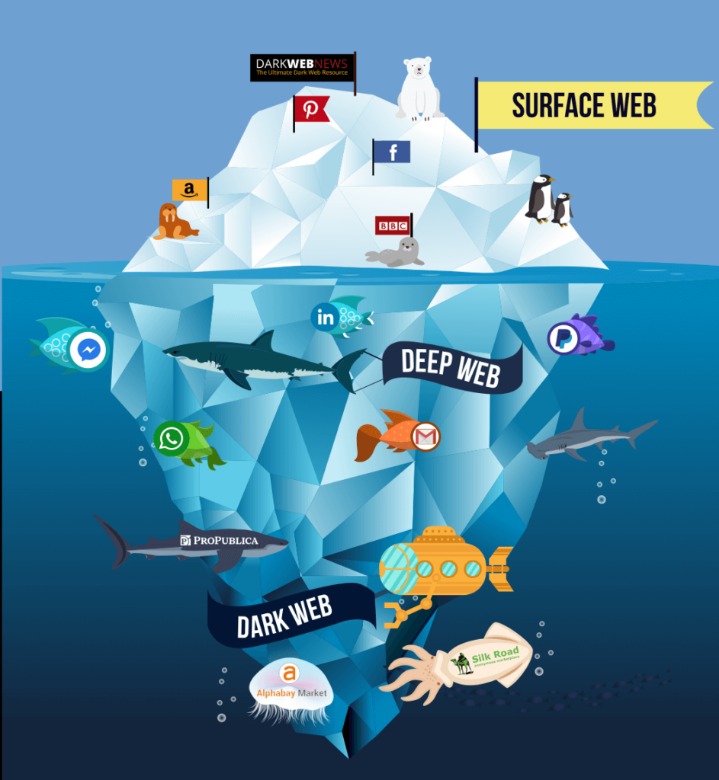
It has been estimated that a large percentage of dark web traffic is related to illegal pornography that includes underage victims. The dark web is a very popular platform for journalists, political bloggers and political news publishers, and in particular, those living in countries where censorship shields most of the internet. You can also find email messages, online bank statements, and much more information on the deep web – information that is usually private and inaccessible by the public on the surface web. For anyone considering exploring the Dark Web, it’s crucial to tread with caution. But for those seeking privacy, freedom of expression, or simply a glimpse into this hidden world, the Dark Web is a fascinating, albeit dangerous, place to explore. Cryptocurrency, particularly Bitcoin, plays a significant role on the Dark Web.
The Intersection Of Cryptocurrency And The Dark Web
- By integrating top-grade security into their operations, organizations can not only reduce their exposure to cyber threats but also reinforce trust in an increasingly data-driven world.
- The deep web refers to any web content that is not indexed or pages that can’t be found with a search engine.
- Note that Hidden Wiki links sometimes lead to unsafe content, so be wary about what you click.
- All of your web page requests on the Dark Web are first connected at random to one of the entry nodes, then bounced off a middle node, and then finally pushed out through an exit node.
- Navigating the dark web requires extra layers of privacy, not just because of its content but due to legal scrutiny.
- Services such as Tumblers are also available on the dark web to help hide transactions.
Get daily tips, tricks, guides, and special offers delivered right to your inbox. Again, these hacking forums sound intriguing but are filled with people who scam and lie for a living. As such, we will not discuss the full range of illicit and extremist content on the dark web. Read on to find out what you’ll find on the dark web—and if it’s worth visiting at all. Plus, you will get reliable advice from Bitdefender cybersecurity experts to help you minimize any negative impact. After reading this guide, you will have a strong understanding of how data transactions on the Dark Web impact your privacy and security.
Why Security Matters When Using Tor
To help protect the information, individuals should change all their passwords, check their credit reports for discrepancies, and inform their bank(s). The dark web helps people to maintain privacy and freely express their views. The popularity of the dark web with criminals makes it a perfect way for undercover police officers to communicate. The dark web’s origins are often traced back to March 20, 2000, with the launch of Freenet, a peer-to-peer sharing network designed to prioritize anonymity.
The mobile app uses DuckDuckGo as its default search engine and is supported by the Orbit framework to provide secure access to the Tor network. VPNs are also used for accessing geo-locked content hosted by streaming services. The best VPN options are paid-for and subscription-based, as many free options will either throttle your speed or collect your data.
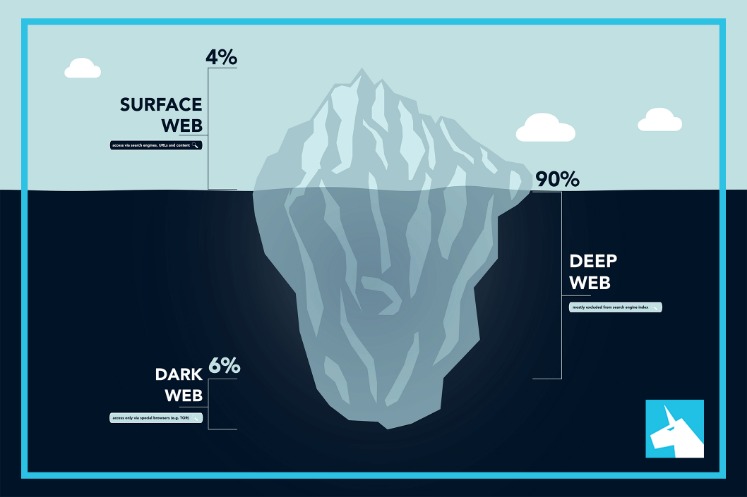

These platforms provide services related to illegal activities, such as hacking tools, malware, ransomware, or services for hire (e.g., DDoS attacks, identity theft). Some sites might offer tutorials or guides for aspiring cybercriminals. The Open Web, also known as the surface web, constitutes the most accessible layer of the internet, readily navigated through popular search engines like Firefox, Google, Bing, and Yahoo.

Education, activism, journalism, and creativity all find refuge here, protected by layers of anonymity. However, it’s vital to approach each new platform with caution—vetting its authenticity, reputation, and purpose before fully engaging. Armed with knowledge, critical thinking, and robust security practices, you can uncover meaningful, valuable content that challenges the dark web’s often one-sided reputation. Finding reliable sites on the dark web can feel like a guessing game—many onion addresses appear cryptic, and their ever-changing nature makes it challenging to build trust. However, the quality of the resources you choose to engage with can make all the difference in ensuring a safer, more productive experience.
- When combined with Tor, for example, a VPN can help prevent IP leaks and make it more difficult for network operators to trace your activities.
- The dark web’s infrastructure allows users to bypass censorship and maintain privacy, which has legitimate uses, such as secure communications for whistleblowers.
- By definition, the dark web is the home to the darker corners of the internet.
- Slide up to the “safest” level, and as well as those settings, JavaScript is disabled on all sites.
- It aimed to provide online privacy by routing internet traffic with a series of volunteer-operated servers, encrypting the data at each step, and making it challenging to trace the user’s identity.
It’s one of the best choices if you want a familiar and private search experience on the internet. China, for example, blocks access to the Tor network entirely, treating it as a tool for bypassing government controls. To get around these restrictions, the Tor network offers an option called bridges. And since most Dark Web sites are used for illegal purposes I am not going to offer any recommendations.
Access to “.onion” domains and anonymous surfing made possible by specialised software like the Tor Browser allows entry only. Cyber threat intelligence (CTI) helps organizations predict, understand, and defend against cyber threats, enabling proactive protection and reducing the impact of attacks. The dark web is dangerous due to the presence of scams, malware, and illegal material.
Facebook offers an onion link to access their services, although you may find logging in difficult, as you’ll most likely appear to be signing in from a different location each time. You must have realized by now that the dark web is a complex and often misunderstood segment of the internet. While it does host some illegal activities, it also provides a platform for secure communication and privacy protection, especially to those who most need it. Law enforcement agencies worldwide monitor the dark web for illegal activities, such as the trafficking of illegal drugs, weapons, and stolen data. Interpol, the FBI, and Europol all have dedicated cyber units focused on dark web surveillance, often leading to high-profile arrests and marketplace shutdowns.
It operates on a hidden network, requiring tools like Tor to navigate its unique structure. Matt Egan is Global Content Director of Foundry, publisher of Tech Advisor, and a passionate technology fan who writes on subjects as diverse as smartphones, internet security, social media and Windows. The content management system into which I am typing this article is on the Deep Web. Meanwhile our company intranet is hidden from search engines, and requires a password. You can browse to it if you know the URL, but it won’t appear in a Google search. Some use similar services such as I2P, for example the Silk Road Reloaded.



