That’s a trick question, because there isn’t even a good free VPN, much less a best VPN. Freebie VPNs will track their users’ online usage, as they make money by selling this tracking info to advertisers and other nosy parties. If top-notch privacy is your goal, yes, you can use the Tor Browser for all of your browsing. Just remember, this only hides your browser-based activities and doesn’t hide any of your other online activities.

Cybersecurity Threats
Understanding the strengths and limitations of each solution helps you select the best tool for your specific needs. Follow this step-by-step guide carefully to ensure safe, anonymous, and secure access to the Dark Web using Tor. The dark web is also unregulated, meaning that it is run and upheld by a vast network of individuals around the world. This network contains thousands of volunteers who operate proxy servers to route dark web requests. As such, no one is responsible for setting rules or ensuring their adherence. This operating model is what makes the dark web such a valuable and appealing tool for cybercriminals and other people with questionable intentions.
What Is The Dark Web? Here’s How To Access It Safely (and What You’ll Find)
“It’s a web browser. Use it like one. It’s that simple,” says Muffett. That’s the desktop edition, but there’s a version for Android and an unsupported onion browsing app for iOS. The dark web is infamous as a dangerous place, where drugs are bought and hitmen hired, but it can be a safe way to browse the internet if your privacy is serious concern. We are committed to ensuring that our website is accessible to everyone. If you have any questions or suggestions regarding the accessibility of this site, please contact us. By embedding these standards into their security framework, organizations can minimize their exposure, fortify their defences and stay one step ahead of cybercriminals.
- Tor uses DuckDuckGo as its default search engine, which is expected for a privacy-focused browser.
- In authoritarian regimes where government surveillance and censorship are widespread, the Dark Web serves as an important tool for political dissent and free expression.
- NordVPN is offering a fully-featured risk-free 30-day trial if you sign up at this page.
- However, remaining anonymous can be invaluable to protesters, civil rights groups, journalists, lawyers, and other vulnerable groups.
- While a website can’t identify you or an ISP can’t decrypt your internet traffic; still, they can still see you using Tor, which can draw some unwanted attention and raise suspicions.
Do I Need A VPN If I Access The Dark Web On My Phone?
It focuses on privacy, censorship resistance, and ensuring free access to content. To access the Freenet-based dark web, you need to install the Freenet application. In 2002, the dark web grew significantly when researchers supported by the US Naval Research Laboratory built and released the Tor network. At the time, the internet was still young, and tracking people was easy while staying anonymous was not. The Tor network allowed safe communication channels for political dissidents and American intelligence operatives around the world. Researchers from Recorded Future estimated that while there are more than 55,000 existing onion domains, only 8,400 (or roughly 15%) of these sites were active.
The terms Darknet, Deep Web, and Clear Net are often used interchangeably, but they refer to distinct parts of the internet, each serving different purposes and accessibility levels. Tails is an open-source Linux-based OS that never writes to the hard drive or SSD. This feature ensures that the programs baked into the OS don’t leave a digital footprint on your machine. Think of it as a whole separate operating system, complete with apps and files, that runs entirely on removable media. If any link looks weird, it likely is and may be a phishing link. Don’t open attachments from untrusted sources, as they are a common vector for spreading malware.

The dark web is full of unknown and potentially dangerous content. Clicking on links there might take you to illegal or harmful material without warning. You should never trust websites and forums on the dark web with your personal information.

Popular Dark Web Search Engines
The anonymity that the dark web provides attracts criminals, hackers, and malicious entities. Visiting dark web sites can expose users to malware, ransomware, and phishing attacks, putting personal and financial information at severe risk. But accessing the Dark Web is not just about downloading and installing the Tor Browser. Users must also navigate through .onion websites—domains that are specifically set up for use within the Tor network. These websites do not appear in traditional search engines, and their addresses are often a string of seemingly random letters and numbers.
What Is The Dark Web? Myths, Realities And Cybersecurity Risks
It is imperative to stay alert and trust your gut when on the web. If you are in a position to report the incident safely, you should report it to the authorities immediately. It’s recommended not to be too vigilant here and leave the investigation to the professionals.

Unverified Content And Hoaxes
The Dark Web is the part of the deep web that is not indexed by search engines, like Google or Bing. For this reason, you cannot browse through these sites using your default search engine. Many social media platforms keep their presence on the dark web, and it is no surprise that Facebook has a .onion portal. Facebook’s dark web version allows users to access the site where it is banned or restricted. Although the social application is known for collecting data on its platform, it does not like sharing the information with others.
On the dark web, you’re expected to find illegal and prescription drugs (including Marijuana). Also, some toxic chemicals are peddled on the dark web that may cause severe damage to the targets. For your optimum dark web safety, you should ensure that once you’re done browsing the Darknet, shut all the browser windows as well as any other content that could be connected. However, there are possibilities that someone can still link personal details to a transaction due to issues like connected nodes, address reuse, and blockchain analytics.

Is Tor Browser Illegal?
Each tool works differently, and some are better suited for specific use cases than others. Don’t log into any real accounts, reuse usernames, or enter any personal details. Treat every site as untrusted unless you’ve verified it from multiple sources.
Trust me to provide you with the expertise and solutions you need. Whistleblowing, the act of exposing wrongdoing within an organization, often requires a secure and anonymous channel. The Dark Web can provide a platform for individuals to share information, documents, or evidence anonymously, ensuring protection against potential retaliation. Whistleblowing enables the exposure of corruption, fraud, or illegal activities that might otherwise remain concealed, contributing to increased transparency and accountability. To protect yourself from Dark Web dangers, it is essential to employ robust cybersecurity measures. Additionally, educating yourself about common phishing tactics and how to identify and prevent them is crucial for staying safe online.
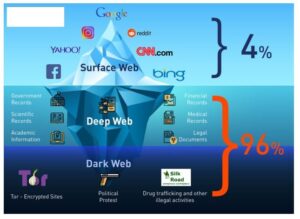
In case you’re wondering how to access the deep web, chances are you already use it daily. The term “deep web” refers to all web pages that that are unidentifiable by search engines. Deep web sites may be concealed behind passwords or other security walls, while others simply tell search engines to not “crawl” them. Without visible links, these pages are more hidden for various reasons. All commonly public-facing websites accessed via traditional browsers like Google Chrome, Internet Explorer, and Firefox are contained here.
However, note that a VPN is not a definitive or comprehensive form of protection. It won’t guard you against all of the many threats that exist on the dark web, from phishing scams to malware and malicious sites. It offers some protection, but you still have to be wary and sensible when browsing the dark web. On its own, Tor obscures your IP address by bouncing online requests through multiple servers, similar to how a VPN routes your traffic through an external server. Websites you visit via Tor will see the IP address of the exit node, not your actual IP, just like websites see the IP address of your remote server when using a VPN.
Understanding that the nature of the internet meant a lack of privacy, an early version of Tor was created to hide spy communications. Eventually, the framework was repurposed and has since been made public in the form of the browser we know today. The deep web rests below the surface and accounts for approximately 90% of all websites. This would be the part of an iceberg beneath the water, much larger than the surface web.