It includes media and archives which cannot be crawled and indexed with current search engine technology. To search for the onion URLs, you need access to a deep web search engine. If you’re new to the deep/dark web, DuckDuckGo’s onion link should be your first port of call. This parent site gives access to all other dark websites through a simple search.
Email Providers
The dark net is famous for being a hub of black market websites for buying and selling products and services. Changing the Tor browser settings can further boost your security levels on the dark web shops. For instance, you can choose the preferred security levels for enhanced protection. The security level is set to ‘Standard’ by default, but you can change it to the ‘safest’ and enjoy more security while accessing the dark web. Having JavaScript enabled on the dark web can cause havoc because it can reveal your IP address to your website.
Understanding onion Links And Mirror Sites
Empire Market is a dark web shop that resembles the AlphaBay marketplace. Its look, design, options, and interface are exactly the exact copy of its competitor, but everything else, including buyers, vendors, and servers, is different. At its launch, the platform accepted payments through Litecoin, but now it has incorporated support for other payment methods like Monero and Bitcoin. The platform also cares about its users and uses PGP encryption and two-factor authentication to secure their data and communication.
This List Contains The Search Engines Most Requested By The Community On The Deep Web:
There are many legitimate uses for dark web services and communication. When the dark web is mentioned online, it is usually in tandem with criminal marketplaces and arrests made by law enforcement agencies. No longer restricted to dial-up, many of us now consider access to a stable high-speed internet connection a critical element of our daily lives. We pay our bills online, check our bank statements, communicate via email, find information, and maintain a presence on social media. Most dark web marketplaces use cryptocurrencies like Bitcoin for transactions to help maintain anonymity.
Your online activity and communications remain private and secret on the dark web. Because of this, some people use it to get around government restrictions, while others use it for illegal activities like smuggling drugs and weapons. Lastly, the dark web is the portion of the deep web that is generally inaccessible and is much larger than the surface web. It relies on P2P connections and requires specialized tools and software. Tor and I2P are the two commonly used tools for accessing the dark web to provide anonymity. For instance, services like ProtonMail and SecureDrop (mentioned above already) have hidden sites for their users who live in countries with high levels of censorship.
Quantum‑Resistant Encryption
Since activists, journalists, and advocates need the dark web to communicate securely, find evidence, and bypass censorship, it remains a tool for privacy and free expression. This sequence offers less anonymity because your real IP address is still partially exposed along the Tor path. Plus, it’s slower since your data travels through the same four steps – entry node, relay node, exit node, and then the VPN server. Your activities on the dark web are not entirely shielded from tracking, and relying solely on anonymity can lead to a false sense of security. The dark web draws not only serious cyber criminals but also law enforcement agents aiming to catch them. Many exit nodes are actually operated by law enforcement and scammers.
- Daniel acts as a dark web search engine to help users find reliable onion sites.
- But again, your ISP won’t be able to see any of the content you’re reading or what you are sending and receiving through the Tor network.
- Data gleaned from ransomware and data breaches is available on the dark web.
- The looming threat of quantum computing has sparked adoption of post‑quantum cryptography in anonymity networks.
- Right now, you can use many cryptocurrency .onion sites to buy or sell all types of cryptocurrencies.
Which Is Better — Tor Over VPN Or VPN Over Tor?
The Hidden Wiki is primarily used as a directory of dark web .onion links, helping users navigate various hidden services such as marketplaces, forums, email providers, and whistleblower platforms. It acts as a centralized hub to access sites that are not indexed by traditional search engines like Google. Many users rely on the Hidden Wiki to find reliable dark web resources safely and efficiently. Navigating the dark web often begins with accessing .onion links—specialized web addresses accessible only through the Tor network, designed to provide enhanced privacy and anonymity online.
Subscribe To Our Newsletter!
Most internet users want to use the dark web safely, but it’s still important to be careful when using any onion browser. Other dark web search engines worth investigating are Ahmia, Torch, NotEvil, and the Onion URL Directory—just type out some keywords for what you’re looking for. Some of these sites can be found through regular web browsers, but you’ll then need to switch over to Tor once you’ve got the onion links you want to follow. Many reputable websites and news outlets like ProPublica and SecureDrop often share official domain addresses of onion sites on their pages. Some users also share links on encrypted apps like Telegram or Keybase that you can check.
WANT TO TRY THE TOP VPN RISK FREE?
However, this feature is only available on iOS, Android, and Windows. The VPN will protect your traffic when you connect with military-grade AES 256-bit encryption. This is high-level protection; no one can intercept your data or activities. This includes military-grade 256-bit encryption reinforced with a 2048-bit DH key and SHA2-384 authentication to ensure your traffic arrives at its destination safely. This adds extra protection since opening Tor itself encrypts your traffic. A virtual private network (VPN) is a good way to mask Tor activities.

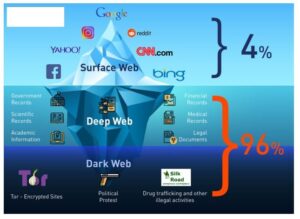
Every communication is encrypted, so even the simplest transaction requires a PGP key. The dark web has flourished thanks to bitcoin, the crypto-currency that enables two parties to conduct a trusted transaction without knowing each other’s identity. “Bitcoin has been a major factor in the growth of the dark web, and the dark web has been a big factor in the growth of bitcoin,” says Tiquet. The dark web is a subset of the deep web that is intentionally hidden, requiring a specific browser—Tor—to access, as explained below. No one really knows the size of the dark web, but most estimates put it at around 5% of the total internet.
George is a seasoned Cybersecurity writer who has been writing guides and news about digital security for over five years. He has worked for several international tech platforms, and his writing and editing expertise has also enhanced over time. He loves covering topics about VPNs, online privacy, and anonymity and shares his knowledge of online security with internet users through his words.

For example, you shouldn’t pirate copyrighted material, engage in terrorism, or share illegal pornography. Some markets are relatively short-lived (thanks to law enforcement), but others are notorious enough that they survive, for instance, Silk Road, AlphaBay, and Hansa. Cryptocurrencies such as Bitcoin have been the dark web currency even before they became available to the general public.

Traders cash in on stolen credit card data dumps, initial access points to vulnerable systems, credentials, and intellectual property belonging to companies compromised during cyberattacks. Try LifeLock free for 30 days to receive notifications if we find your personal information on the dark web and help protect against identity theft. However, engaging in illegal activities on the dark web, such as purchasing illicit goods, remains illegal, just as it would be on the surface web. Radar Rundown Hiding your IP address is one of the best ways to protect your online activities from … It is a good website for finding out which websites are currently working. If you need a listing of currently active websites, contact their support, and they will provide you with that.
Privacy Advantages Of The Hidden Wiki

Always use PGP keys when available to verify the identity of marketplaces or services. Another good practice is to cross-reference links with multiple sources to confirm consistency. Avoid clicking on links posted in random or unmoderated sections, as these are often the most dangerous.
It’s used by 50+ news organizations, including ABC, Bloomberg News, CBC, and The New York Times. However, Facebook’s dark web version will still log your data, so keep that in mind. While your IP address is hidden, the site can still collect information you share on your profile.