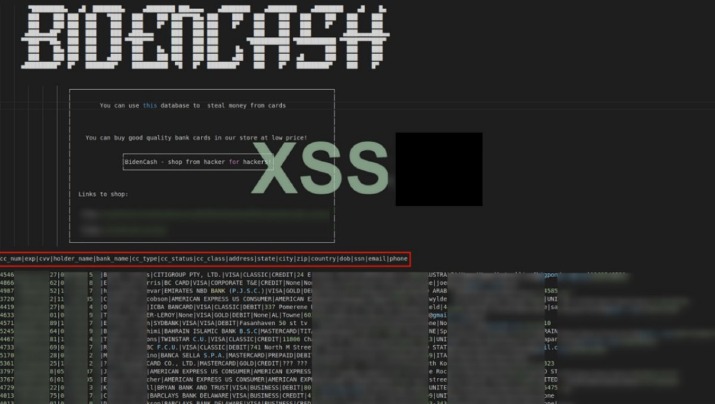
Phishing is a method used by scammers to trick users into trusting them and providing their personal information or account data. Next, let’s explore how individuals can access the Dark Web safely, while minimizing personal risks and vulnerabilities. Join us as we break down and discover the methodologies of card fraud using our dark web monitoring tool, Lunar.
Spyware And Malware

Lunar, our dark web monitoring tool is designed to empower individuals and businesses in this battle against cybercrime. With features like real-time alerts, data breach monitoring, and comprehensive dark web post monitoring, Lunar helps organizations stay ahead of deep and dark web threats in an increasingly hostile digital environment. In recent years, I’ve observed some shifts in how carding is carried out—changes that mirror broader developments in both technology and threat intelligence research. Notably, cryptocurrency has become a valid option for carding operations, whether through exploiting stolen crypto wallets and accounts or using stolen credit card details to purchase cryptocurrency.
- Many services now offer real-time monitoring and alerts that can help you catch fraud early.
- Russian Market has consistently remained one of the most popular and valuable data stores on the dark web.
- This anonymity allows criminals to conduct illegal activities without fear of being traced by law enforcement agencies.
- So next time you log in to your banking app or swipe your card at the store, do it with the silent confidence of someone who knows the secret behind digital security.
- From the data D3Labs has examined so far, about 30% appear to be fresh, so if this applies roughly to the entire dump, at least 350,000 cards would still be valid.
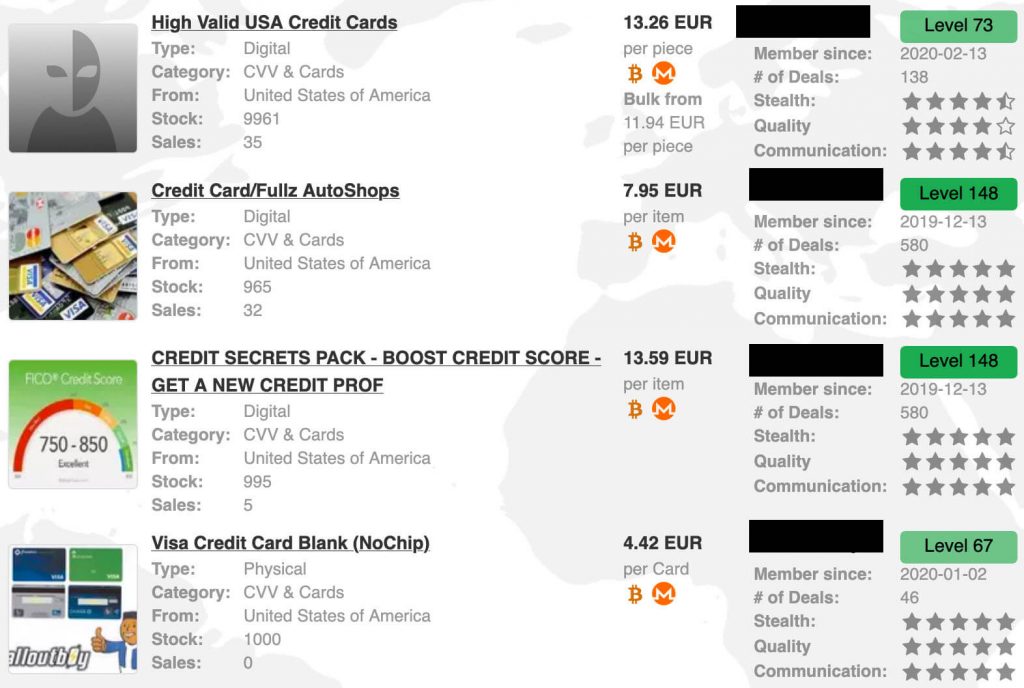
The key is catching this activity before large volumes of card data make it to market. What many don’t realize is that much of this stolen data comes from large-scale breaches rather than individual card skimming. Social Security numbers and other national ID numbers are for sale on the dark web but aren’t particularly useful to cybercriminals on their own. That merchant specifically mentioned that using a stolen card on a store that uses Verified by Visa (VBV) will likely void the card. Verified by Visa is a service that prompts the cardholder for a one-time password whenever their card is used at participating stores. The average price of a cloned, physical card is $171, or 5.75 cents per dollar of credit limit.
The process, also called skimming, allows them to make physical purchases at ATMs or retail stores. Unlike online fraud, this type of theft is harder to detect because the transaction appears as a regular swipe. These details often land there after data breaches, phishing attacks, or malware infections that steal information from unsuspecting users. If your credit card number appears on the dark web, it means someone has likely leaked or stolen it—and now it could be traded, sold, or used without you even knowing about it.
Unmasking The Underground: Navigating The Threat Of Dark Web Credit Card Marketplaces
Use a service, like Flare, that allows you to monitor the dark web for any mentions of your organization’s information, including business credit card numbers. Flare, for example, enables you to automatically scan the clear & dark web for any leaked or stolen account credentials. By doing this, you can find your credentials for sale on the dark web and secure them before they are exploited. Fraudsters can use the stolen information for unauthorized transactions, identity theft, or resell the data on other platforms. The scale of this leak underscores the persistent vulnerabilities in global payment systems.

Why Monitor Deep And Dark Web Credit Card Sites?
In addition to just selling credit card details, some threat actors offer a “complete package” often referred to as “Fullz”. Fullz includes full personal details as well as financial details such as bank account details or social security numbers, which can be used for a full account takeover or identity theft. Payment information is stolen in a variety of ways before it ends up on the dark web. Many payment card numbers are stolen via data breaches; threat actors compromise payment sites, allowing them to stealth credit card numbers. Others might be stolen through phishing attacks on companies, stealing their customers’ payment information. Some credit card details are stolen using devices called skimmers, which are placed in card readers specifically to steal payment information.

Are Dark Web Marketplaces Organized Like Online Shopping Sites?
Additionally, phishing scams and malware-infected websites are utilized to trick unsuspecting victims into providing their credit card details unknowingly. It is imperative for individuals to remain vigilant and exercise caution to protect their credit card information from falling into the wrong hands. Additionally, securing transactions with a 3-D Secure ACS (Access Control Server) solution plays a pivotal role in bolstering the overall fraud prevention strategy.
Keep A Check On Your Bank Accounts

Even if a cybercriminal manages to snag your password, an additional layer of authentication—be it a fingerprint, text message code, or an authentication app—significantly raises the barrier to entry. The most expensive card details, which cost about $20, were in Hong Kong and the Philippines and the cheapest, some at just $1, originated in Mexico, the US and Australia. Dark web posts and offers of this size are usually scams, so the massive dump of cards could easily be fake data or recycled data from old dumps repackaged under a new name. According to Kaspersky, the Risepro infostealer, which is also targeting cryptocurrency wallet data, is spreading through software cracks, game mods and key generators. It’s also good practice to keep an eye on your credit report so that you can spot and report any errors or accounts someone is trying to open in your name.
Theirtactics involve sophisticated schemes, such as relaying stolen NFCcard data, registering fraudulent POS terminals by money mules, andconducting large-scale unauthorized transactions. These criminalsexploit the convenience and widespread adoption of NFC technology,targeting vulnerabilities in payment systems and taking advantage ofpoor security measures. Cybercriminals can exploit NFC vulnerabilities to access personal information stored on devices or NFC-enabled ID cards, leading to further misuse of the victim’s identity. NFC fraud can result in significant financial losses, especially when attacks are scaled. Forexample, the “Ghost Tap” attack allows cybercriminals torelay stolen NFC payment data to make unauthorized purchases. Eventhough individual transactions may be small, the cumulative lossescan be substantial when applied at scale.

Is It Illegal To Access The Dark Web?
These systems can often identify when stolen card data is being tested before major fraud attempts begin. This type of malware silently infect payment terminals and exfiltrate card data in real-time. Use encryption to protect customer data and secure your payment processing system. The more secure your information is, the less likely it will be to fall into the hands of a threat actor. The payment information is then posted for sale on the dark web where other threat actors can purchase and use it. Unfortunately, needless to say, credit card fraud of this type is not a victimless crime.
Dark Web Alert — 29 Billion Passwords, 14 Million Credit Cards Stolen
This victory against cybercrime dealt a severe blow to the criminal underground, disrupting operations on one of the most prolific dark web platforms. You’re probably wondering how things like a PayPal account login or credit card details end up on the dark web. People unexpectedly have their card cloned, their identities stolen, or their accounts hacked. Most stolen card details end up on the dark web marketplace for a quick profit, and this can happen before you even know about it. After hackers collect this info, they post it to one of the dark web marketplaces where it can be sold. The leaked data from the BriansClub hack showed that stolen cards from U.S. residents made criminals about $13 to $17 each, while those outside the U.S. sold for up to $35.70, Krebs reported.
- Becoming familiar with their techniques can help you retain control over your money.
- Another unique feature Brian’s Club has is the auctions it offers during which users can reserve, bid, and outbid other users who want to purchase exotic BINs.
- Cybercriminals use stolen Track 2 data, which is intercepted by ATM skimmers or acquired on the Dark Web, to record it on ‘white plastic’ and then use it on POS terminals.
- It is understood that the data included such highly sensitive information as the primary account number of the credit cards concerned, along with expiration dates and the card verification value, CVV2, security code.
Stay In Control—Use Privacy Virtual Cards To Mask Your Card Details
The dark web may be an ever-present undercurrent, but with the right strategies and awareness, you can navigate the digital landscape confidently and securely. Here’s to making savvy, well-informed choices in an era where every swipe, click, and tap has the power to shape your financial destiny. They employ reputation systems, encrypted transactions using cryptocurrencies, and detailed product listings. However, unlike mainstream sites, these platforms operate in complete anonymity and outside legal oversight. So next time you swipe your card or tap your phone at checkout, spare a thought for the high-tech battle that keeps your money safe in an era where your data’s value could rival a blockbuster movie plot.
Getting a dark web alert doesn’t mean you’re automatically a victim of identity theft. But having your personal information exposed on the dark web can make it easier for others to access and use your identity. These stolen cards have value because they can be used to purchase high-value items or gift cards, which can then be resold for cash. These cards have a security chip installed, providing better protection than those with just a magnetic stripe. Since European countries have quickly adopted the EMV trend, the theft cases and percentages are lesser than in the US.
Any action you take based on the information found on cgaa.org is strictly at your discretion. CGAA will not be liable for any losses and/or damages incurred with the use of the information provided. These dumps are sought for physical use, enabling activities like cash withdrawals from ATMs.



