Notably, Abacus explicitly forbids highly dangerous goods, including weapons, explosives, and exploitative material, which has helped maintain a relatively favorable reputation among its user base. Receive helpful security alerts, time-saving tips and technology trends directly in your inbox. Our solution combines intelligence and search capabilities to help detect and alert you when your company login information shows up on the dark web. That way, you can change passwords or make other updates before a serious IT security breach occurs.
Unmasking The Dark Web Economy: Key Hubs And Cybersecurity Implications
Additionally, you can opt for Subgraph OS as a second option to Tor. The early version of Tor was created to mask spy communications. In due course, the framework was remodeled and made public as a secure browser. An easy way to find content on the dark web is to receive a link from someone who already knows about it. No one is hiding here—they’re just guaranteeing that people in censored countries can read the news without being flagged.
For many people, the answer is by using regular websites such as Reddit. The moderators enforce a strict policy against posting links to illegal products or services, so you’re more likely to find safer dark web addresses here. Keeping an eye on the dark web is no easy task, but law enforcement and cybersecurity pros have some pretty advanced tools up their sleeves. Machine learning is another big player here—it helps by analyzing data to predict and identify suspicious behavior much faster than a human ever could.

Facebook Onion Site
Even passive activity on these sites can contribute to criminal networks. For instance, buying fake documents may indirectly support larger operations involving trafficking, extortion, or organized crime. Farwa is an experienced InfoSec writer and cybersecurity journalist skilled in writing articles related to cybersecurity, AI, DevOps, Big Data, Cloud security, VPNs, IAM, and Cloud Computing. Also a contributor on Tripwire.com, Infosecurity Magazine, Security Boulevard, DevOps.com, and CPO Magazine.
Impact On Businesses And Cybersecurity

I possess a keen interest in exploring and understanding the intricacies of malware, Advanced Persistent Threats (APTs), and various cybersecurity challenges. My dedication to continuous learning fuels my passion for delving into the complexities of the cyber world. And if you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics. As I’ve mentioned, the dark web isn’t just a place of eternal torment, teeming with drug dealers, human traffickers, and a hitman. It’s also used by journalists, advocacy group members, and political refugees in hiding.

Method II – VPN Over Tor

However, note that the site only uses non-sensitive and public data for the metrics. The Tor Metrics is a good place to get more information about the Tor project. It collects data from the public Tor network and archives historical data of the Tor ecosystem.
It’s been a constant back-and-forth between cybercriminals and law enforcement, with each new site trying to be smarter and more secure than the last. Today’s cybercriminals spread their activities across multiple platforms, making them harder to track and shut down. The dark web can be a dangerous place and may not be for everyone. There are also some excellent ways to protect your privacy from most bad actors. Take some time to decide if this is the right option for you before downloading the Tor browser.
- For small and medium-sized enterprises (SMEs), the consequences of compromised credentials, data breaches, and reputational harm can be devastating.
- A budget-friendly VPN service allowing users to access dark web safely anytime, anywhere, and on any number of devices they want.
- Unlike traditional e-commerce websites, these marketplaces rely on encrypted networks like Tor (The Onion Router) and cryptocurrencies such as Bitcoin to conceal user identities and transactions.
- Their bank, along with law enforcement, would have complete insight into their purchase.
First Deep Web Black Markets
Cyber criminals are posting and selling verified Zoom accounts on the dark web. The links being auctioned included email addresses, passwords, meeting IDs, host keys and names, and the type of Zoom account. Launched in 2011, Silk Road was the first modern darknet market that operated on Tor as a hidden service. We have simplified the cybersecurity assessment process and made it accessible for all businesses.

Top 5 Deep Web Black Markets
The website looks organized and has a clean, sleek, easy-to-use UI. You can find featured listings on the homepage and browse the products of your choice. There’s also a search bar that you can use to search for any particular product or vendor.
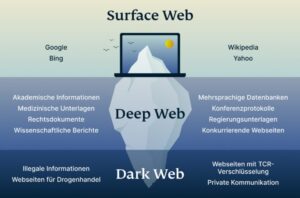
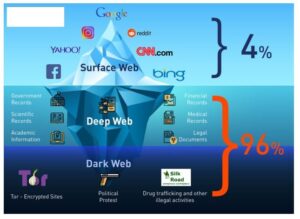
For example, you can only find your Facebook friends, photos, and other information by logging into your Facebook account and finding the information there. On the deep web, you can find such “private” information on web pages. So, that means that the number of pages increased by over 100 trillion in just over three years. Hypothetically speaking, Google may be aware of well over 200 trillion individual pages (these are obviously NOT all indexed in the search engine).
In 2020 alone, American consumers lost more than $56 billion to credit card fraud and identity theft scams. While some of these markets were shuttered by law enforcement agencies – some took the easy way out with exit scams. Here are some of the now-defunct dark web markets that were notorious for cybercrime.
As law enforcement agencies’ tactics improve, some markets respond by introducing more security features, like mandatory encryption or invite-only access. But no matter how polished or professional these sites seem, the risk of getting scammed — or tracked — is always high. Using a dark web search engine is a great step towards enjoying a more secure experience while shopping on the platform.

Fortunately, in Hidden Wiki, every website is followed by a brief description so that the user knows what to expect. You can also take a look at the blogs & essays section if you want to find some nifty coding resources. At first glance, Tor doesn’t look that different from your regular browser – it has a search bar, lots of quick-launch icons, the peeled onion icon smack in the middle of the screen. Well, now it’s time to fire up Tails and do a little bit of tinkering.