That it is an open source project that is in charge of handling suggestions and comments anonymously. On the other hand, we have Tor2Web, which is a service that helps people who are not yet in the Tor network. As you continue your online journey, keep expanding your knowledge of digital privacy and security. The more you understand, the better equipped you’ll be to navigate safely and confidently, no matter where your curiosity leads you. Dark web forums are online platforms that can only be accessed using anonymous networks, mainly Tor….

What Is The Best Uncensored Search Engine?
- Torlinks (2019) and The Hidden Wiki evolved with V3 .onion support, reinforcing directories’ role in structured navigation.
- With tools like Cyble Vision, it helps organizations stay protected of cyber threats, including dark web monitoring, providing critical insights for better cybersecurity management.
- I’ve used it to find reliable .onion services like ProtonMail quickly, and its Google-like UX feels familiar, easing the learning curve.
- One of Daniel’s impressive features was the built-in functionality that showed whether a particular dark website is online.
- Uncensored search engines break down these barriers by not tailoring results based on past searches or user profiles.
While it does not have the premium features of engines like Haystak, its strength lies in accessibility. Anyone with the Tor browser can open Torch and begin searching instantly. In 2025, Ahmia remains one of the best ways to access real onion sites while reducing unnecessary risks. However, engaging with illegal content or using dark web sites for unlawful purposes is a criminal offense. Always stay within legal boundaries and use the dark web responsibly.
With 100,000 web pages of search results that include coverage of the deep web and darknet marketplaces and forums, it is a very popular search engine used by cybercriminals. Phobos has a very simple user interface that only includes a search bar. It is also the fastest one out of all the search engines we cover in this post. Z-Library is the globe’s most extensive illegal library, which claims to provide access to over 11 million ebooks. The library has been operational since 2009, providing ebook files in various file formats without their copyright protections. The Z-Library functions as an intricate network of hundreds of interconnected web domains and is available through TOR and I2P platforms.
Is It Safe To Use A Dark Web Search Engine?
With its robust encryption, Forest VPN protects your data and identity, ensuring a safe browsing experience. Hackers spend a lot of time on the dark web, and it’s not too difficult to get access to hacking tools and data leaks in this part of the internet. However, it’s much harder to get at the people who are doing the uploading and downloading. DuckDuckGo is the default search engine inside the Tor browser, and once you turn on the Onionize toggle switch in the search box, you’re able to use it to find dark web links. These typically come with “.onion” after them, rather than something like “.com” as on the standard web.
Be Mindful Of Legal Implications
Despite its legitimate uses, the dark web has earned its reputation due to the illicit activities it hosts. It is a hub for black markets where criminals trade illegal goods and services, such as drugs, weapons, counterfeit currency, and stolen data. Many cybercriminals use the dark web to buy and sell hacking tools, exploit kits, and malware.
OnionLand features a clean, intuitive design and offers search suggestions to streamline the dark web browsing experience. It indexes both old V2 onion addresses and I2P content, and it allows users to search across both the clearnet and dark web by using multiple indices. This flexibility lets you filter searches to focus exclusively on the dark web or include results from both realms. DarkWebLinks focuses on listing only the most recent v3 .onion links, ensuring users access updated and secure dark web sites. As many dark web sites have yet to transition to the newer v3 format, the site will add these once they do. While the free version is solid for general searches, the premium version can offer a more refined, expansive experience for power users.
To mitigate these risks while exploring the dark web, it is crucial to use a reputable dark web browser like Octo coupled with proxies for an added layer of security. Keep your software always up-to-date, exercise extreme caution when clicking on links or downloading files, and avoid sharing personal information. Understanding the inherent dangers of the dark web and taking proactive safety measures are essential for a secure dark web experience. Exploring the dark web can provide valuable insights and essential privacy, but it requires careful, informed navigation. By selecting trusted search engines, crafting precise search queries, and diligently verifying sites, you can greatly enhance your safety and effectiveness. Remember, good digital habits—such as maintaining anonymity, avoiding risky behavior, and staying vigilant—form the foundation of secure dark web exploration.
Is It Illegal To Use A Dark Web Search Engine?
- By taking these steps, you can navigate the invisible web safely and efficiently.
- This makes it perfect for retrieving content that has been deleted or modified on the surface web.
- This setup ensures anonymity while leveraging NotEvil’s privacy-centric, no-log design.
- Users who are simply curious about the dark web may find themselves in risky situations without realizing it.
- Understanding how to use Tor is one of the best ways to familiarize yourself with the Deep Web and what you can really do.
- This marked the beginning of efforts to explore the vast, unindexed parts of the internet.
This makes it one of the most reliable tools for discovering a wide variety of content. Whether someone is looking for forums, marketplaces, or simple community pages, Torch often delivers a broad set of results. The sheer scale of its database is what has helped it maintain relevance despite competition from newer engines. You enter a query, and the engine returns onion links with clear descriptions. This makes it much easier to avoid clicking random or suspicious links.
How Does Haystak Work?
Once you’re on the website, click “Download Tor Browser.” Then, select the appropriate version for your operating system and follow the prompts to complete the installation. For severe issues (e.g., child exploitation), use secure channels like law enforcement tip lines via clearnet proxies, but maintain your anonymity with Tails OS. Avoid direct engagement; document evidence offline and consult ethical guidelines to prevent backlash. Report via the engine’s community mechanisms, like Ahmia’s GitHub for blacklisting or NotEvil’s volunteer reports, or submit to Tor Project forums anonymously.

What Precautions Should I Take When Exploring The Dark Web?
Kilos also adapts to the evolving nature of dark web markets, helping you discover new sources as they emerge. Popular search terms on Kilos include narcotics, firearms, and fraud-related items, reflecting its role in catering to diverse user needs. Torch allows you to search for blogs, marketplaces, forums, and onion services across the Tor network without tracking or censorship.

Though they have their limitations, most of the time you’ll see irrelevant or spammy links for your search results. RiseUp is a top dark web website that offers secure email services and a chat option. It was created in 1999 as a secure communication platform for people and groups working on liberatory social change. The platform is protected from government interference and malicious attacks to protect the user.
More Security Articles
Dark web forums are online communities where individuals participate in discussions on a wide range of subjects, from technology and privacy to more illicit matters. That’s why security teams need continued visibility into the dark web which enables them to mitigate the risk of data leaks, preventing further damage. Cybercriminals often leverage the anonymity to leak sensitive information, like stolen credentials, credit card numbers, or company data. This process makes tracing the user’s location and activity nearly impossible. The core functionality of the dark web relies on onion routing, a method that encrypts and routes user communications across multiple servers, known as nodes. It has a reputation for being fast and effective, though the content it indexes varies widely in quality and legality.
✅ Final Thoughts – Safest Way To Use The Best Dark Web Search Engines In 2025
Hacker services against banks and other financial institutions are offered there. The purpose was to protect U.S. army soldiers and agents in the field, but also politicians who held secret meetings and conversations, which contained the highest security measures. Those who access the dark web do so via the Tor (The Onion Router) browser. The dark web addresses are a randomly-scrambled sequence that generates URLs, mostly hard to remember ones. For example, the URL of Silk Road is rather unintelligible and may look something like “gan4arvj452janndj4a76.onion”.
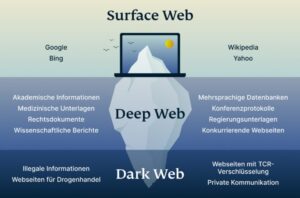
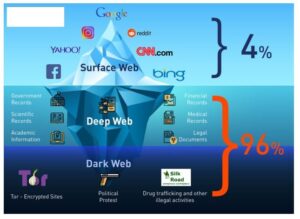
Even the best privacy tools are only effective when patched against the latest threats. The Directory of Open Access Journals is a deep internet search engine that provides access to academic papers. The deep web is made up of content that typically requires some form of accreditation to access. Examples include library databases, email inboxes, personal records (financial, academic, health, and legal), cloud storage drives, and company intranets. If you have the correct details, you can access the content through a regular web browser.