Buyers would pay in Bitcoin, hoping to receive counterfeit bills that could pass as real. However, many were left empty-handed or received poorly made counterfeits that were easily detectable. These scams not only resulted in financial loss but also carried significant legal risks, as attempting to use counterfeit currency is a serious crime. In the end, the scammers themselves often became victims of their own fraudulent schemes. Counterfeit money refers to imitation currency produced without the legal sanction of a government, typically with the intention to deceive or defraud. While counterfeiting has existed for centuries, the digital age has made the tools and resources counterfeit money sale online needed to produce fake currency more accessible than ever before.
More From The Los Angeles Times

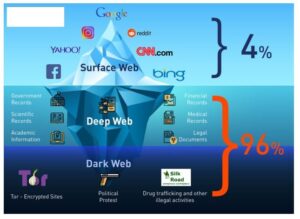
The dark web is part of the internet that is not indexed by standard search engines like Google, Yahoo, and Bing. It means you cannot access websites on the dark web with regular browsers like Firefox or Chrome. Instead, you need a specific configuration, software, or authorization, such as Tor, to access it. Some markets even sell privacy tools, but you are more likely to run across counterfeit prescription pills and stolen identities.
Common Dark Web Scams
We are based in Brussels and we specialize in regulatory risk compliance services covering the Eurozone. Pideeco combines professional Regulatory knowledge and technical expertise to safeguard your business’ reputational and operational risk. Our unique customer-centric approach helps us build strategical and legitimate cost-efficient remedies.
How To Use The Online Pranks?
If you know the right websites, you can easily access a tremendous amount of information, including research articles, news stories, and more. You can buy directly from the official website, which is safe, or contact support staff to set up escrow for your purchase. Our support staff will assist you if you’re unfamiliar with using escrow services. Recent advances in photographic, computer, and printing technologies, along with the availability of low-cost equipment, have made the production of counterfeit money relatively easy. However, we stand out from other companies by producing super undetectable counterfeit notes. The sale of stolen ‘personally identifiable information’ or PII is also common on the dark web, used to create and sell fake IDs.
What Happens If Your Data Is Sold On The Dark Web?
Another essential security feature is that all incoming and outgoing data from the app is encrypted, including any private and public keys involved. I2P, or the Invisible Internet Project, allows you to access the ordinary and dark web. Specifically, the I2P darknet is accessible, while the Tor network is accessible through the Orchid Outproxy Tor plugin. While it might appear tempting to venture into the dark web, it’s crucial to understand that the risks here are far more severe compared to the deep web. Some of the deep web sites do not use standard top-level domains (TLD) such as .gov, .com, .net, etc. No user names are tied to actual identities, and no moderation like one may find on Reddit.

Although knowing which country counterfeits are available is helpful, products must be purchased first and subsequently shipped to be found at a border. Thus, estimation of product origins from dark markets and measures of seized goods might also vary because they capture products at different supply chain stages. The scam ecosystem has been booming around the world, with criminals honing a handful of strategies to trick victims into voluntarily sending their money into the abyss. And as the cash—or, typically, cryptocurrency—flows in, a set of digital services and infrastructure offerings have increasingly emerged. The scam economy helps criminals with everything from creating fake social media pages to buying SIM cards—and, crucially, with money laundering.
Is It Illegal To Visit And Use Dark Websites?
Such new data is generated by first randomly selecting a listing of that category and finding the k (5) nearest neighbors of that listing within the feature space. Then, one of the neighbors is selected at random, and a new data point is created at a random point between the two listings in their feature space. Both under- and over-sampling methods were implemented in python using the package “imblearn” (Lemaître et al., 2017). Next, we utilized the “LinearSVC” classifier with an “l2” penalty (the default regularization parameter used to reduce complexity in the model and avoid overfitting) using a tenfold cross-validation procedure.
- If your personal data ends up for sale on the dark web, it can lead to serious consequences like identity theft, financial fraud, or unauthorized access to your online accounts.
- These networks often operate across borders, using global shipping systems, fake companies, and shell corporations to distribute counterfeit bills.
- These listings often include detailed descriptions, user reviews, and even shipping guarantees.
- Once implemented, prolonged data collection could be easily maintained, providing us with regular details on counterfeits.
- Active for a decade since 2014, it is a widely used credit card shop used to source stolen credit card information such as dumps, CVVs, Wholesale Accounts.
Stolen And Leaked Personal Data
Understanding the process involved in obtaining fake IDs and documents highlights both the complexity and the significant risks involved. Despite the apparent ease, purchasers are continuously exposed to potential scams, fraud, interception by law enforcement, and severe legal consequences. Criminals use underground marketplaces to sell these counterfeit goods, deceiving unsuspecting buyers into purchasing fake products. One popular method used for money laundering on the dark web is the use of cryptocurrencies, such as Bitcoin. These digital currencies offer a level of anonymity that traditional banking systems do not provide, making them an attractive option for criminals seeking to launder money. Another challenge is the need for international cooperation and information sharing among regulators and enforcement agencies.

Facebook Onion Site

Its .onion site provides an additional layer of privacy and security for users accessing their Bitcoin wallets or exploring transaction data, especially useful in regions where cryptocurrency sites might be monitored or blocked. Blockchain even has an HTTPS security certificate for even better protection. The website has an advanced search filter and an easy-to-use interface, which makes it easy to find what someone is looking for. Whether local or international goods, research documents, banned drugs, you name it, everything is available on this dark web platform (that’s one of the reasons why this should be monitored for security purposes).
- For example, Whonix’s virtual workstation machine connects to the internal virtual LAN.
- Previous studies about dark markets sometimes encountered holding prices, which vendors use to mark out-of-stock listings, preventing their removal from the market (Soska & Christin, 2015; Wegberg et al., 2018).
- Note that engaging with the content in any way is not only distressing but could also put you at legal risk.
- Public awareness campaigns also play a crucial role in helping individuals recognize fake bills and avoid falling victim to scams.
These “credential dumps” allow criminals to access online accounts, steal identities, and commit fraud. Most buyers and sellers use the Tor network, which hides IP addresses and locations. Doing so makes it harder for authorities to identify who’s behind a purchase or a listing. Vendors often build up reputations through ratings and reviews, just like sellers on mainstream platforms. To reduce scams, many markets also use escrow systems, where the site holds the buyer’s payment until they confirm the item has been delivered.
Regulatory Measures To Prevent Illicit Activities
Here, you’ll find links to various resources, including educational archives, private forums, anonymous services, and more. The successful takedown of Wall Street Market in 2019 involved simultaneous operations coordinated by law enforcement agencies in Germany, the Netherlands, and the United States. Authorities seized extensive data, cryptocurrency wallets, and arrested several key administrators and high-profile vendors. Purchasing fake IDs or fraudulent documents on the dark web involves specific steps designed to preserve the anonymity of both the buyer and the seller. The process is structured similarly across most dark-web marketplaces and generally includes using privacy-focused cryptocurrencies, anonymous communications, and secure delivery methods. In conclusion, the pathway fake documents take to arrive on dark web markets is complex and multifaceted, involving cybercrime, sophisticated forgery techniques, and thriving digital black markets.
He is scheduled to be sentenced on August 24 and faces a maximum penalty of 20 years in prison. Actual sentences for federal crimes are typically less than the maximum penalties. A federal district court judge will determine any sentence after taking into account the U.S.