
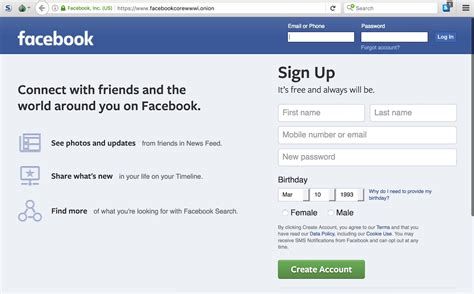
The Daniel site also had a status check feature that updated users on which sites were active. Unfortunately, the site’s admin could not keep up with the time demands and has taken down the links on the site as of August 2023. Few countries operate with strict censorship on citizens’ internet access, preventing them from getting information in or out. BBC is the most popular news source and is the best example of restrictions on International media. The dark web version of Facebook isn’t malicious, but if you log into it, it will keep your data. However, there’s no guarantee that all the links on this site are working. mark it means it has been verified as a scam service and it should be avoided. Stay safe and informed as you explore the deeper layers of the internet.}
Extortion tactics, like “living off the land” attacks, will also become more common, as cybercriminals exploit existing systems to carry out their attacks. There are good reasons for the dark web websites to exist, but also reasons to be cautious when visiting websites on the dark web. Overall, law enforcement is making strides in its efforts to combat crime on the dark web. With the use of advanced technologies, undercover operations, and legislation, law enforcement is making it increasingly difficult for criminals to operate in the shadows of the internet. The dark web is estimated to be significantly larger than the surface web, but much of it remains hidden or inaccessible.
Encrypted Messaging Apps And Private Communities
These services form the communication backbone for sensitive conversations in high-risk environments. WhiteHouse Market has earned a reputation for its robust vendor verification and user-friendly design. It employs escrow services and PGP encryption for communications, significantly reducing the risk of scams. DarkMarket is among the largest darknet marketplaces by volume, offering a broad selection of goods, from software to electronics. It is known for strong encryption protocols and anti-DDoS protections, ensuring reliable access and user anonymity. Reddit’s .onion link provides secure and anonymous access to the popular discussion and content-sharing platform through the Tor network.
Credential-Based Attacks
There’s even an option to set a timer on your most sensitive messages so they disappear after a set time period. However, Facebook’s dark web version will still log your data, so keep that in mind. While your IP address is hidden, the site can still collect information you share on your profile. It lets you search both clearnet and dark web sites, but it blocks all trackers, doesn’t use your location data, and never stores your search history. But despite its many benefits, it’s sadly just a matter of fact that the dark web can be a dangerous place.
The Rise Of Malicious AI
- From uncensored libraries to secure whistleblowing channels, these platforms can offer benefits difficult to find on the clear web.
- Malicious employees can steal company information and sell it on the dark net.
- One of its best features is Anonymous View, which is a free proxy that masks your identity while you’re browsing sites.
- Cyble’s platforms, such as Cyble Vision, monitor the dark web for emerging threats, providing real-time insights to protect organizations from cybercrime.
- The competitive landscape remained unchanged, with no significant innovations reported.
Since these markets operate on the Tor network, they require .onion links that are not indexed by regular search engines. The dark web is home to many online marketplaces, offering everything from digital goods to rare items. If you’re searching for a reliable dark web marketplace, We The North Market provides secure transactions, encrypted communications, and a low 5% vendor fee. In this guide, we’ll break down the top dark web markets and how to stay safe while using them.
If you only want to mask your IP address and don’t need to access the dark web, then going online with a VPN is much easier and faster than using Tor. These domain names are not registered with a central authority but are instead derived from cryptographic keys. Following the NYT, the BBC launched a dark web “mirror” of their international edition in 2019. Note that some features of the normal website are not available on the .onion version, including BBC iPlayer. Experienced users typically prefer marketplaces with robust vendor rating systems, detailed feedback options, and transparent dispute resolution processes.
Cypher Marketplace
Disable JavaScript and other potentially risky browser features unless necessary, as they can be exploited to reveal your identity. Avoid downloading files or opening attachments from unknown sources, as these can contain malware. Use strong, unique passwords and enable two-factor authentication where possible. The Tor Browser looks and feels similar to a regular web browser but is configured to prioritize privacy and security by default. It blocks browser trackers and resists fingerprinting, which helps maintain your anonymity while browsing.
Explore key dark web statistics, including the number of people using the dark web, things you can find there and the types of activities it hosts. We will also share some tips for safe browsing so you can keep your data safe. Like any other browser, you can search for a relevant keyword using its search bar, and it will show you results if its database has any relevant websites stored. Ahmia has a very strict policy against abusive content, and any link with such content, if reported, is added to a blocklist and isn’t shown in future search results.

Preparing To Access The Dark Web
A top-of-the-line VPN network that ensures maximum security while accessing dark sites online. This includes military-grade 256-bit encryption reinforced with a 2048-bit DH key and SHA2-384 authentication to ensure your traffic arrives at its destination safely. This adds extra protection since opening Tor itself encrypts your traffic. ActiveX and Java frameworks are susceptible to being exploited by hackers.

Acronis Cyber Protect Cloud: New Version C2505
The platform’s commitment to user privacy is evident in its robust encryption protocols and its stance against data logging. Whether users are seeking specific information, resources, or merely exploring out of curiosity, Ahmia delivers comprehensive and relevant search results. It offers a secure platform for whistleblowers and sources to share information without fear of retaliation. This framework is often referred to as IT strategy or digital strategy. By adopting these strategies, businesses and individuals can better protect themselves against the ever-evolving threats of the dark web.

How To Access Onion Sites
With its sleek design and user-friendly interface, Grams offers a streamlined shopping experience for Tor users. For those interested in the statistics and technical aspects of the Tor network, Tor Metrics offers a wealth of data. This initiative by the CIA is a testament to the growing importance and acceptance of the Tor network in ensuring secure access to information.
Founded in 2005, Exploit.in is one of the oldest Russian-language dark web forums still in operation. This platform connects cybercriminals involved in fraud, hacking, and RaaS deals. With tight access controls and a preference for Russian speakers, Exploit.in maintains a high signal-to-noise ratio, ensuring only serious actors thrive. With over 15 billion records sourced from nearly 936 datasets, BreachForums remains one of the largest dark web forums for data leaks. Its escrow service and user-ranking system make it attractive to elite cybercriminals. Bitcoin Fog is one of the most popular and longest-running crypto mixers on the darknet.

Using a reliable antivirus to scan your device is worthwhile if you spot suspicious spikes in system resource usage. This isolates any potential malware and prevents cross-contamination with your personal data. Using Tails OS can further security, as all your data is reset every time you close the device. BlackCloud offers encrypted file storage specifically optimized for the Tor network. The service emphasizes privacy with zero-knowledge encryption and no registration requirements. My tests showed reliable performance for smaller files, but larger transfers can be slow due to Tor’s limitations.
Is It Illegal To Use The Tor Browser?
However, while it may help users find basic links organized by topic, it offers no actual search functionality or dynamic indexing. Users must manually scroll through categories, many of which include outdated or broken links. Because it doesn’t use a crawler or ranking algorithm, OnionLinks is static and highly dependent on manual submissions, which makes it unreliable for current or time-sensitive research.



