People often turn to the dark web for privacy or to access information not available elsewhere, ranging from anonymous forums to censored content or specialized marketplaces. Understanding its dual-use nature is essential for navigating its risks and leveraging its benefits responsibly. For businesses, proactive measures, including regular cybersecurity risk assessments and dark web monitoring, are vital to safeguarding sensitive information. While accessing the dark web itself is not illegal in most countries, engaging with illicit activities or even visiting suspicious websites can attract the attention of law enforcement agencies. On the legitimate side, the dark web provides a platform for whistleblowers, journalists, and activists operating under oppressive regimes. For instance, platforms like SecureDrop allow individuals to anonymously share sensitive information with news organizations, bypassing censorship and surveillance.
- Not to be confused with the riskier Hidden Wiki page, Wikipedia on Tor serves as a vast repository of information.
- TorBook aims to be a privacy-focused alternative to mainstream social networks.
- And it’s still essential to use strong passwords and two-factor authentication (2FA) to help keep your account secure.
- Few countries operate with strict censorship on citizens’ internet access, preventing them from getting information in or out.
- From drug trafficking to arms deals to stolen data, the dark web provides a marketplace for many illegal goods and services.
Don’t Provide Personal Information

You can look for information on /r/deepweb, /r/TOR, or /r/onions, of which the latter is useful to find hidden wikis and more. Many of these Reddits have rules prohibiting linking to illegal sites and services, so you likely won’t find anything illegal there. But accessing the Dark Web is not just about downloading and installing the Tor Browser. Users must also navigate through .onion websites—domains that are specifically set up for use within the Tor network.
- As a result, your dark web use may draw unwanted scrutiny from your ISP or law enforcement.
- The U.S. Federal Bureau of Investigation (FBI) arrested Ulbricht in October 2013, but imitators still arise, many much larger.
- While the dark web is famously known as an illegal platform for criminal activities, that’s not all about this part of the web.
- Central to navigating this hidden internet are “.onion” sites, unique websites that end in .onion instead of .com or .org.
The most interesting thing about NordVPN is its built-in Onion over VPN feature. It encrypts your traffic at the entry node and changes your IP address. This means you will get a VPN’s security and enjoy the anonymity of the Tor network simultaneously. ActiveX and Java frameworks are susceptible to being exploited by hackers. Since you are navigating in uncharted territories with all the myriad threats today, you’ll have to disable them in your network settings to stay safe.
Popular Dark Web Search Engines: An Overview Of Ahmia, DuckDuckGo onion, Torch, And Not Evil
Ransomware as a service, stealer malware as a service (SMaaS), and phishing-as-a-service operations are thriving and helping fuel illicit add-on services. There are also myriad support services that help lower the barrier to entry in executing these attacks, or to help make attacks more efficient. These include crypting services, dropper services, and exploit kits for RaaS and SMaaS, according to Carroll. There’s a growing emphasis on scalability and professionalization, with aggressive promotion and recruitment for ransomware-as-a-service (RaaS) operations. “More than 200 cryptocurrency accounts allegedly owned by the ransomware group were frozen by law enforcement, stripping the group of significant profits,” an AFP spokesperson tells CSO. International policing groups are working to disrupt several major platforms through joint efforts.
StartPage – User-Friendly Dark Web Search Engine Like Google
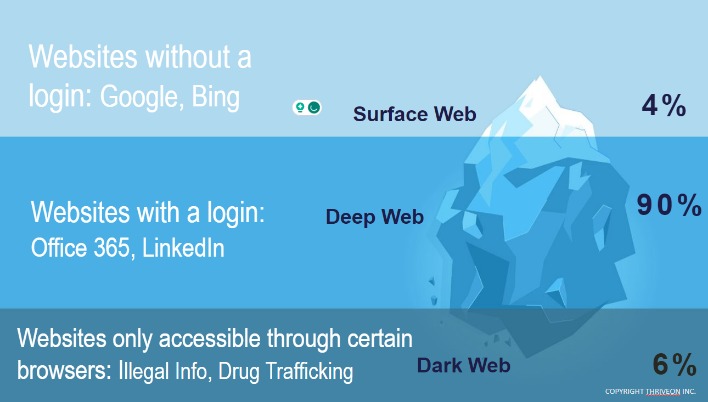
Without visible links, these pages are more hidden for various reasons. Tor Network, short for “The Onion Router”, is a network consisting of volunteer servers that encrypt Internet traffic and route it through multiple nodes. This technology makes it very difficult to track the identity or location of users. This is particularly useful for people living in countries with internet censorship, journalists, activists or simply for those who want to protect their privacy. The dark web is a part of the internet that isn’t accessible with regular browsers or search engines like Google and Bing.
Download Tor Browser
Onion sites are websites on the dark web that use the “.onion” top-level domain instead of “.com,” “.net,” “.gov,” etc. Onion sites use The Onion Router (Tor) software to encrypt their connections and enable anonymous communication. The dark web is the unregulated part of the deep web, which encompasses all parts of the web not indexed by search engines.
Excavator Search Engine

Organizations like WikiLeaks and investigative journalists use dark web platforms to exchange sensitive information safely. Privacy-conscious users, including journalists and political activists, use the dark web to communicate securely, especially in oppressive regimes. Cybersecurity risk assessments and regular monitoring of dark web activities are essential to identifying and mitigating threats before they result in significant damage. If you stumble upon illegal content or believe you’ve become a victim of a scam, it’s important to report it to the appropriate authorities, just as you would in the physical world. Besides offering a secure connection, Forest VPN is designed to use less battery, reducing your carbon footprint. Its competitive pricing ensures that robust privacy protection is as affordable as a cup of coffee.
We Helped Patch A Chromium Bug That Could Leak Your Real IP — Here’s How
The website has an advanced search filter and an easy-to-use interface, which makes it easy to find what someone is looking for. You can choose the best darknet (.onion) website that suits you and start surfing. For safer browsing, it is highly recommended to also use a VPN and antivirus software. While exploring the dark web can offer valuable privacy benefits, it’s crucial to understand common risks and how to manage them effectively. In short, even with Tor, there’s no perfect anonymity online, but there are efforts to claw back our power online, says Lewis.

How To Safely Access The Best Dark Web Sites – Quick Guide
As we all know, websites on the surface web end with common suffixes such as .com, .org, .edu, and .gov. When browsing through Tor on the dark web, however, the suffix is .onion. It’s fitting because Tor itself stands for The Onion Router, a reference to the multilayered (like an onion’s skin) encryption it uses to keep users anonymous. The answer, of course, is by using dark web browsers like the open-source platform Tor. If you’ve done any amount of reading about the dark web, you’ve probably seen that iceberg illustration about the World Wide Web.
CSO Executive Sessions: How AI And LLMs Are Affecting Security In The Financial Services Industry
It hosts encrypted websites, often used for privacy, anonymity, or illicit activities. The surface web is the open part of the internet, which includes publicly accessible websites and resources. Search engines index all the web resources on the surface web, so you can search for them online. You just need standard browsers like Chrome, Edge, and Safari to open websites on the surface web. The dark web often connotes illicit activities like illegal drug sales and hacking. However, it also supports legitimate uses like protecting free speech and accessing information in censored regions.
Top 10 Dark Web Search Engines Of 2025 For Safe & Private Access
The release of Freenet in 2000 is considered by many as the start or founding of the dark web. University of Edinburgh student Ian Clarke created Freenet as a thesis project. Freenet was originally intended to provide a way to anonymously interact online, providing ways to communicate, exchange information and files, and to otherwise communicate incognito. But human trafficking, illegal pornography featuring underaged victims, money laundering, and assassinations are also examples of the darkest corners on the dark web.
It’s still illegal to commit crimes while connected to Tor, regardless of whether or not you think you’ll be caught. Swiss based ProtonMail is an encrypted email service that is quite popular with the cryptocurrency community. It’s a paid service, and while it’s extremely secure you will need another email address to sign up, which can leave traces of your true identity without you realizing. OnionShare is one of the best tools for that purpose, whether on the surface or deep web. The service remains free to use, and the secure design prevents access to third parties, eavesdroppers, and other malicious agents. When you’re dealing with sensitive information, nothing feels truly anonymous or private.